Your (almost) complete guide
Hello, Hoodies!
We’re overdue for a paid stack, so here we go.
We’re continuing with the Hacking Applied series, and today we’re going over Hashcracking!
What is a hash?
It’s a string that’s the result of a hashing function.
What’s a hashing function? A 1 to 1 function where every unique input (is supposed to) produce a unique output of fixed length.
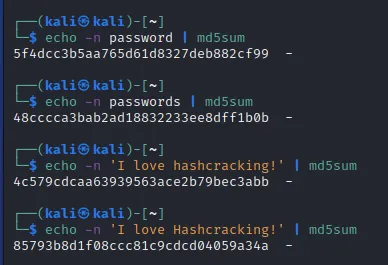
This is the md5 algorithm (which you’ll be familiar with if you studied your Net+ and Sec+). Even though it’s deprecated, it’s still incredibly common today.
Notice that each input has a different output, all of a fixed length. Changing one character changes the output dramatically.
Hashcracking is the process of going in reverse – starting with a hash and ending with an input.
But that’s impossible!!!
Yes it is. And that’s what makes it so much fun.
If you find this interesting and you want to start you Cyber Career, become a PAID HOODIE in the STACK. Everything you need to go from ZERO to HOODIE and into your first cyber job.
Now, let’s dive into hashcracking. Take it away, HoodieX!
Hey there Hoodies!
I am back with another red team article. This time I will explain the tools and techniques that we can use to create a password wordlist/crack hash. This will mostly cover the top tools used to generate password lists, identify hashes, and crack password hashes. Let’s have a quick look at the tools we are going to use,
Password Generate
cewl
ttpassgen
cupp
Hash Identification
Haiti
Hashid
Online Tools
Password hash cracking
John
Hashcat
CrackStation (online)
Why password is important
As we all know the password is a key to unlocking something. If we have the password to a system/application we don’t have to use any system/software vulnerabilities to get access. So once we know the password, we can directly access the system, and it will also bypass any firewall that may exist (with little odds).
How to generate a password list
Before generating a password list. We must know the key points of generating passwords. The password list may vary for each individual/application/system/whatever. This means that for each target we have to create an individual wordlist based on the target, whether the target is a human or technology.
Now on to password generating. First, we have to do some passive information gathering about our target (human) because the user is always a human. But it will not always be the case that we will know our target. In this situation, we have to use guesses to select the right word list.
Let’s say that the target has a website. In most cases, people’s passwords are names/numbers that they have used on their website/social media. This method will be helpful for this type of password generation.
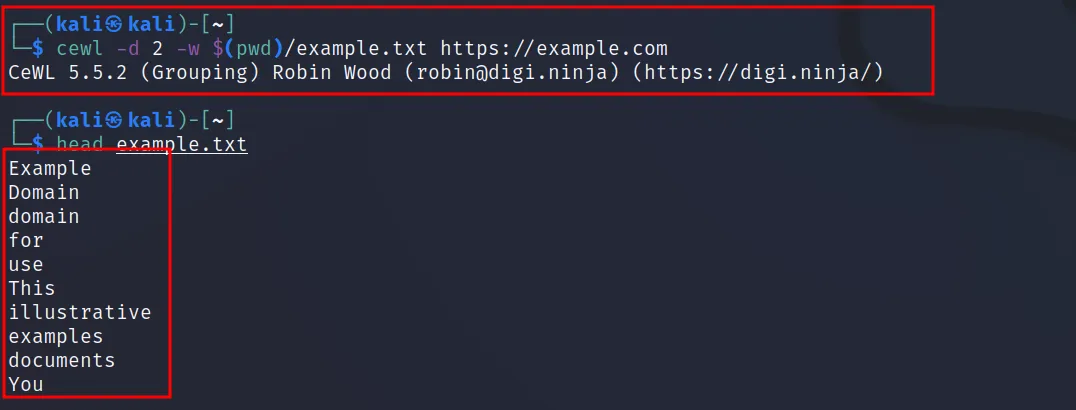
Execute this command ‘cewl -d 2 -w $(pwd)/example.txt
https://example.com
‘, this will scrap all the words from the given site with a spider depth of 2. This tool comes by default installed in Kali Linux, in case you don’t have it run ‘sudo apt install cewl‘ to get this.
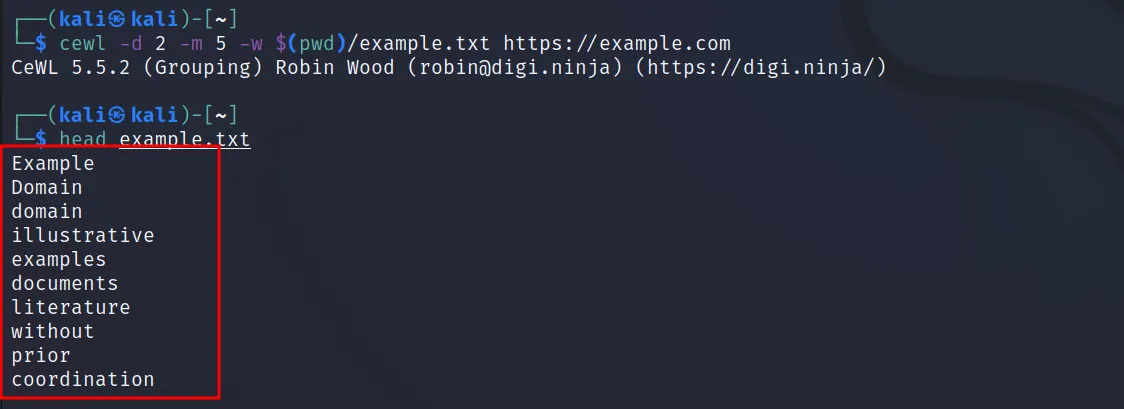
This will spider and scrap all the words with the length of 3 characters. But if we want to scrap only the words with 5+ characters we can do this by adding ‘-m <n>‘ in the command.
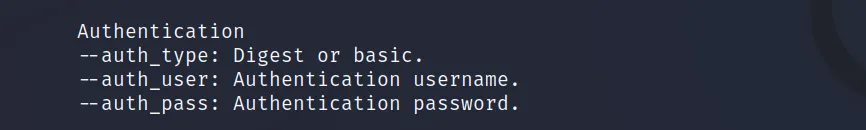
We can also use a username/password for authentication when using this tool. For this, we will have to use the below commands.
It also supports proxy, custom headers, and user agents. You can check all the use of this tool using the help ‘cewl -h‘ command.
Now, what can we do to create a password list of number sequences and other? In this case, we will use the tool TTPassGen. It uses regex to generate a wordlist. Here we can combine the generation with another list as well.
This tool is not installed by default in Kali Linux. So we have to install it manually using python-pip.
Command Executed: ‘sudo pip3 install ttpassgen‘
If you also see the same error. First, install the python-pip itself.
Command Executed: ‘sudo apt install python3-pip‘
Now we can install it.
Command Executed:’sudo pip3 install ttpassgen‘
Let’s see the use of it.
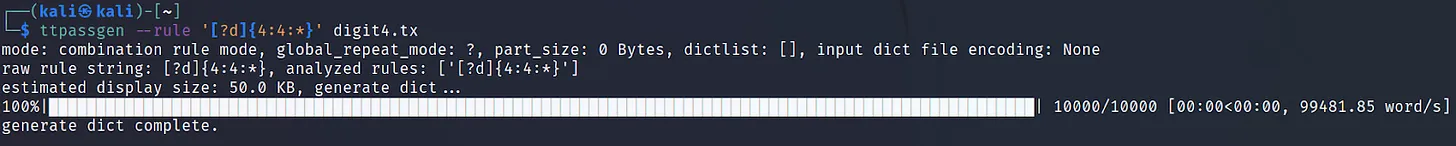
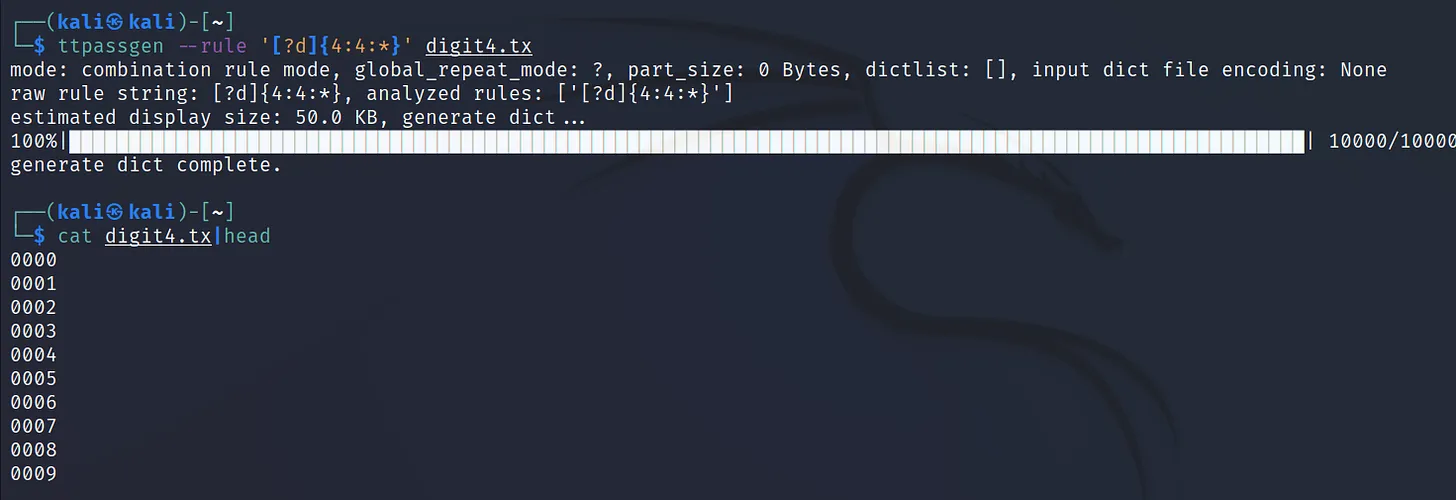
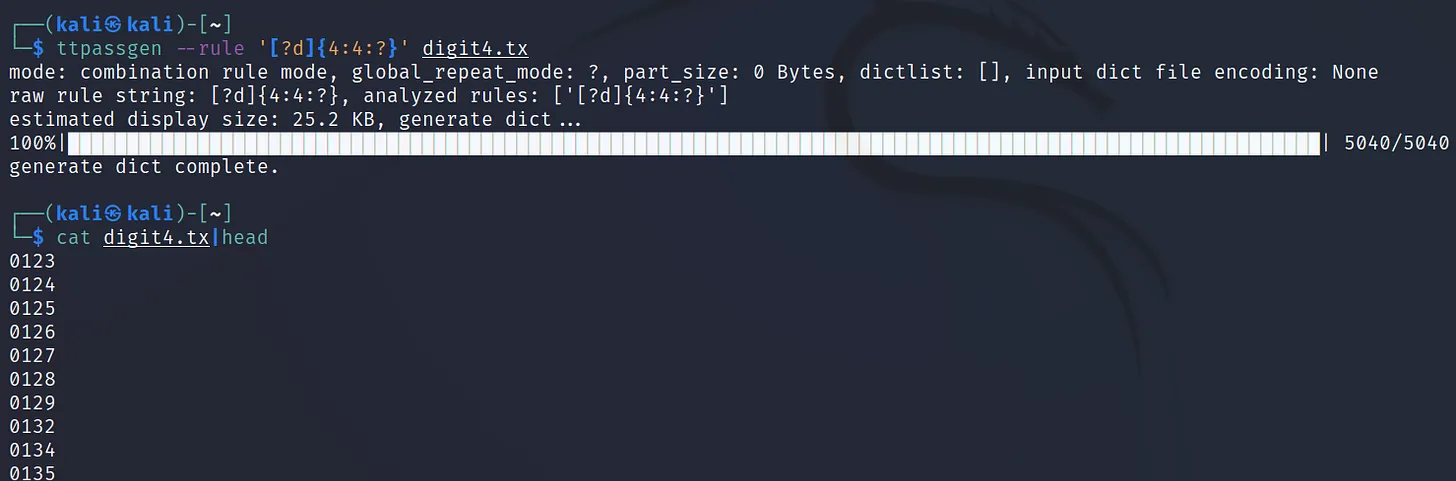
Execute the command ‘ttpassgen –rule ‘[?d]{4:4:*}’ digit4.txt‘
Command Breakthrough:
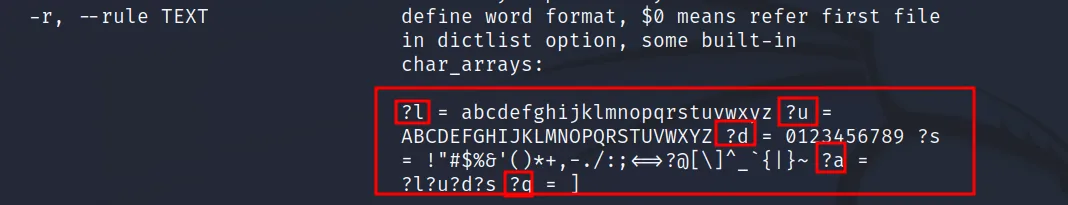
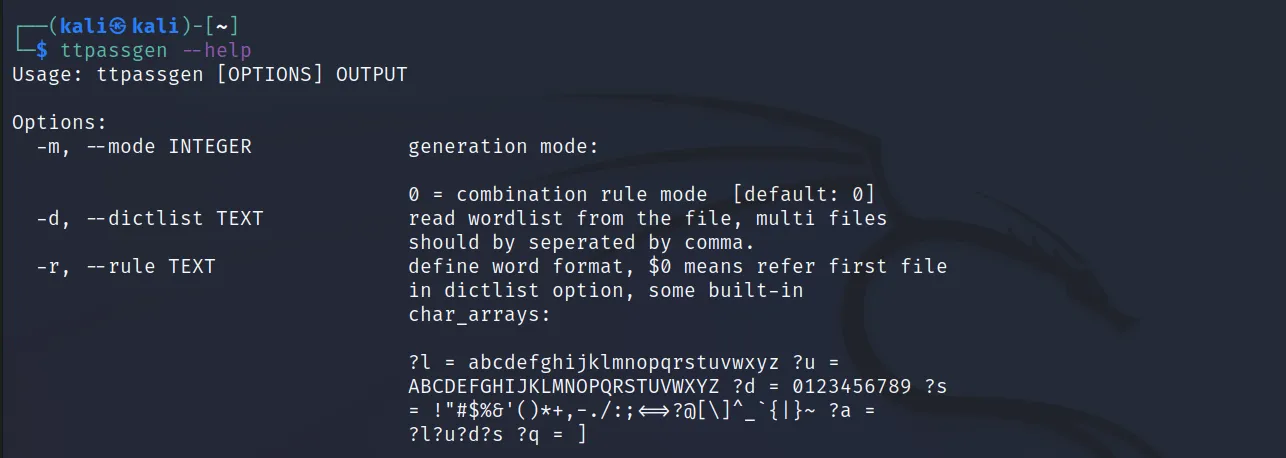
–rule : This is used to set the rule of password generation. For example, ‘?l ‘means all the lower case alphabet, the ‘?u‘ means all the upper case alphabet, ‘?d‘ means all the digits, ‘?s‘ means all the special characters, ‘?q‘ square brackets, and lastly ‘?a‘ for all the combo.
After we have used the array [], we can set the length limit using {min_repeat: max_repeat:repeat_mode} and the (*) is the wild card, for every sequence. If no wild card is specified by default it will choose (?).
Let’s see the difference between the two.
(*)
(?) or none
You can learn more about the rules from the official GitHub page. Let’s continue
Sometimes we may have to create a list of some wordlist and some custom digits, for example, hello123, hello124, or two wordlists and concatenate the word with some other characters like hello-hi, hi-hello. In this case, we can use the method explained below. Let’s see it in action.
Execute this command ‘head -100 /usr/share/wordlists/rockyou.txt > list.txt‘ to take the first 100 lines of RockYou.
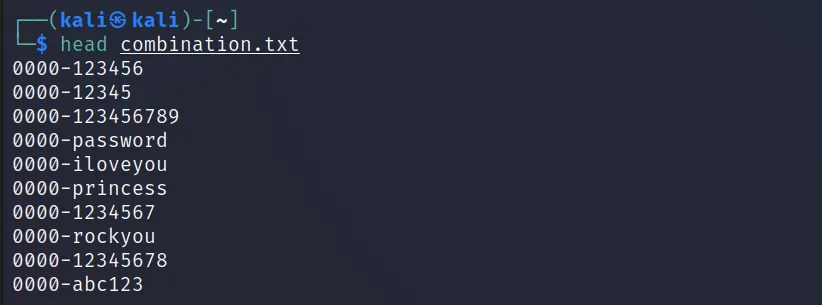
Now execute this ‘ttpassgen –dictlist ‘digit4.txt,list.txt’ –rule ‘$0[-]{1}$1’ combination.txt‘ command.
Command Breakthrough:
–dictlist is used to select wordlists, we can select multiple wordlists with a coma (,) separated. And the indexing for the wordlists will start from 0 to the number of wordlists. For example, for the first wordlist, the number will be $0, for the second $1, for their $2, and so on.
[] is the array where we can put anything. Look at the output, it will make it clear. Notice the (-) added in between.
That’s it for this tool, for more information about this tool, you can also check out the help menu, and their official github page.
Now for the third tool of password generating that we must know is ‘cupp’. You can install it using ‘sudo apt install cupp‘ in your Kali Linux.
This tool asks for some information (name, address, etc) about the target, and creates a word list based on the data. You will better understand it by doing it.
Execute this command ‘cupp -i‘, (i) for interactive mode.
I haven’t inserted the right info, but if you do the password list will look like real passwords. And out of the three methods I showed you, this one has the best possible chance of success.
But this may work for a very specific target. What about the random target? In this case, we can use pre-generated wordlists by other infosec experts. Just like the rockyou.txt.
This is not in the Kali Linux or in the Debian repository. So you have to download it from Github.
Execute the commands,
”’
git clone https:// github.com/BlackArch/wordlistctl.git
cd wordlistctl
pip install -r requirements.txt
”’
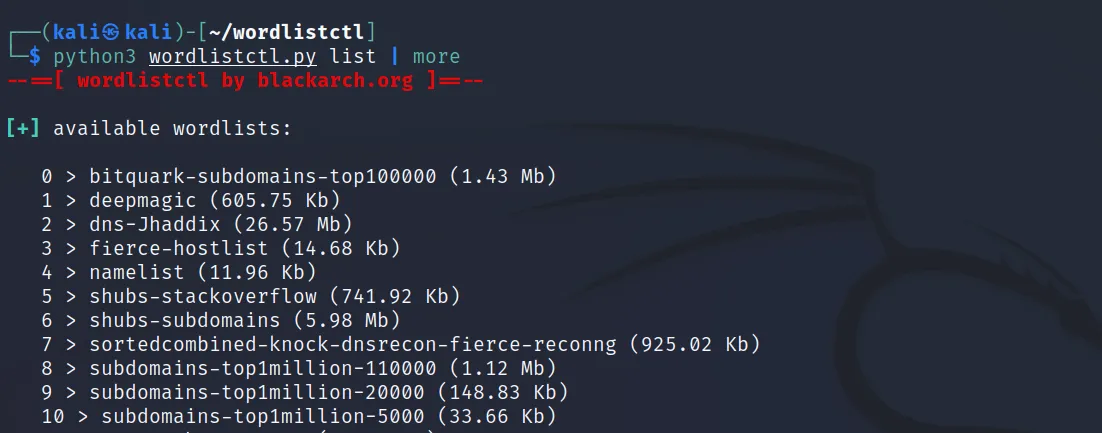
Now we can run this tool with ‘python3 wordlistctl.py‘. Now execute this ‘python3 wordlistsctl.py list‘ command. This will allow us to see all the wordlists it has to offer.
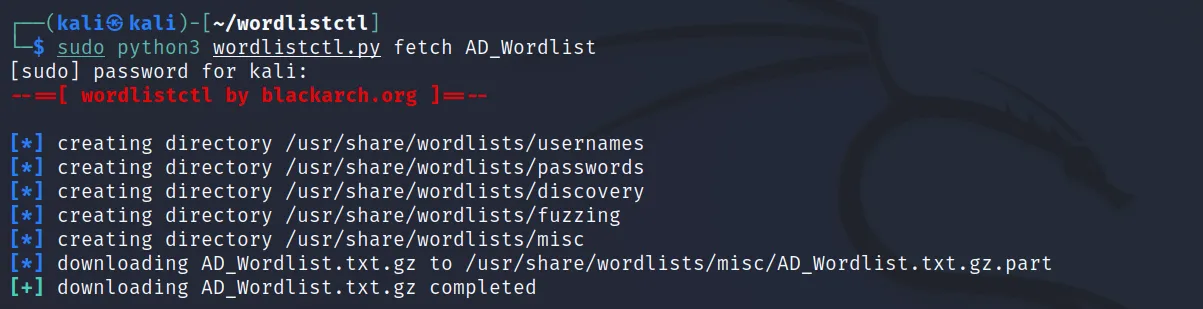
Let’s download a user/pass combo for AD. We have to use the ‘python3 wordlistctl fetch <name>‘ command to do that.
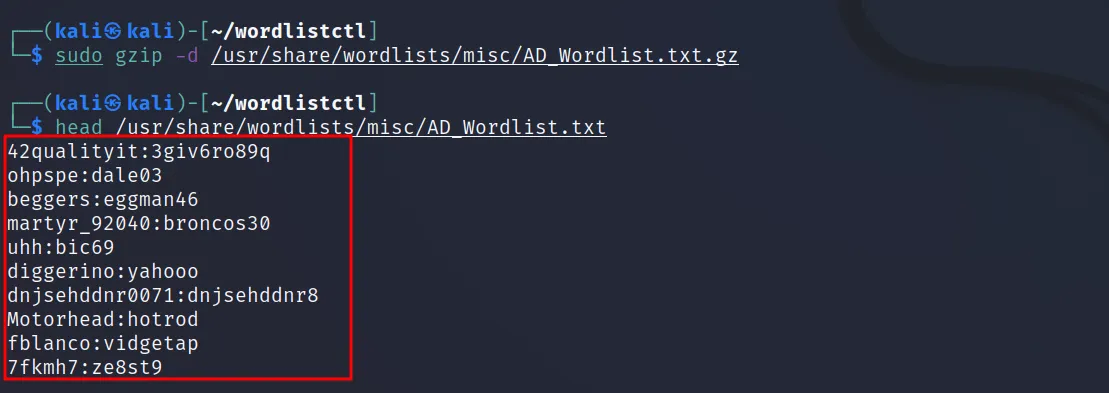
Now let’s unzip the file, and check the combo.
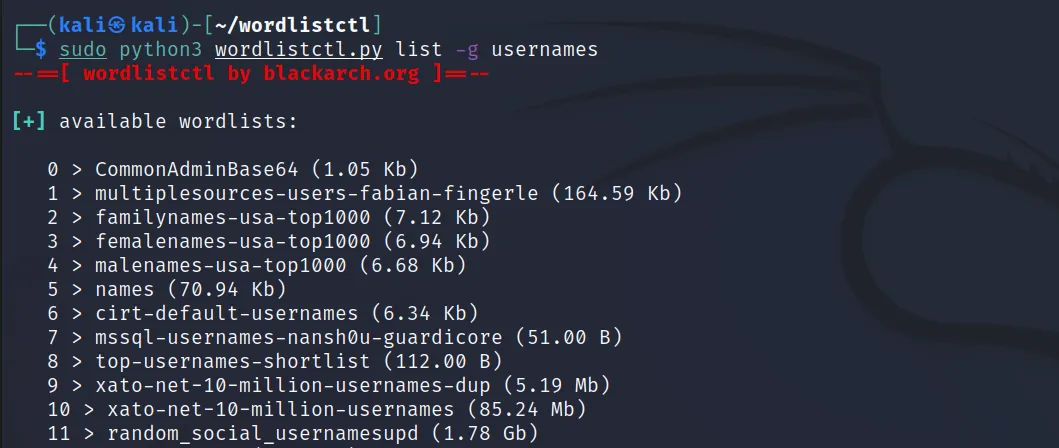
We can use the ‘-g‘ for searching through specific wordlists. For example, ‘usernames’, ‘passwords’, ‘discovery’, ‘fuzzing’, ‘misc’.
Command Executed: ‘sudo python3 wordlistctl.py list -g usernames‘
Ok, I hope you got the idea. You can manage the rest on your own. Just try out all the commands. Lastly, you need to know about the SecLists.
It’s a list containing wordlists for discovery, fuzzing, passwords, payloads, usernames, web shells, and more. This is mostly used by Bug Hunters for web pentesting.
You can download this from GitHub.
Now let’s move on to the next step.
Hash Identification
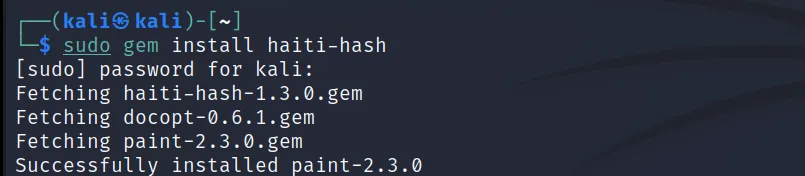
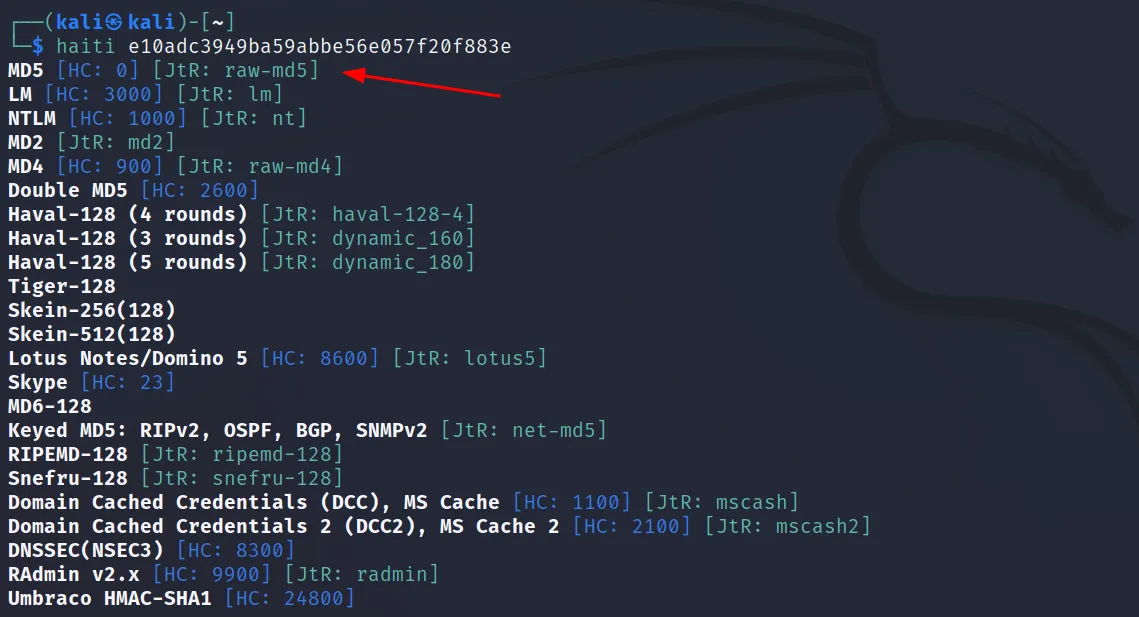
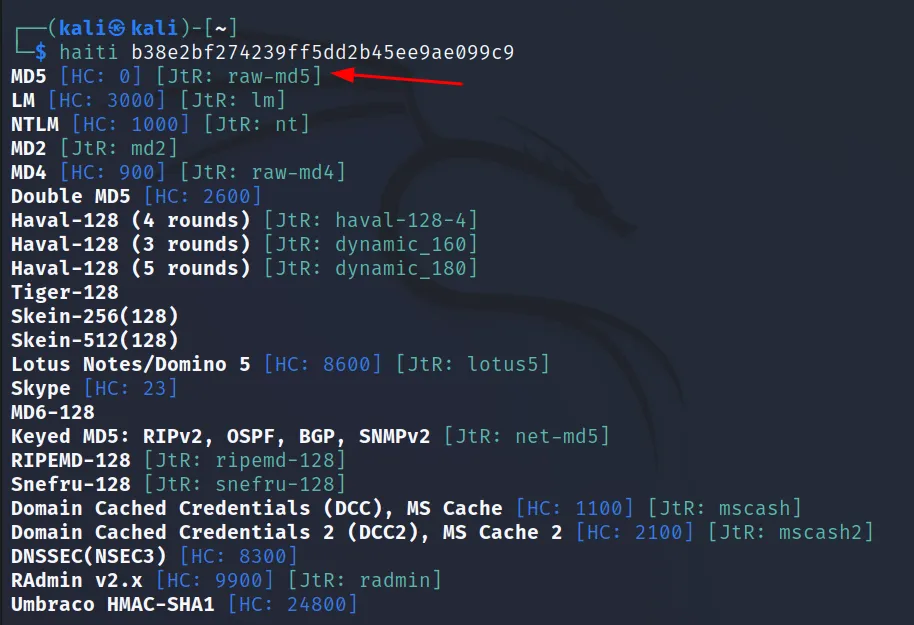
Before we crack any hashes, we must know the hash type. We can use some offline/online tools to identify the hash. For this, we will use ‘haiti‘.
Install this using the ‘sudo gem install haiti-hash‘ command.
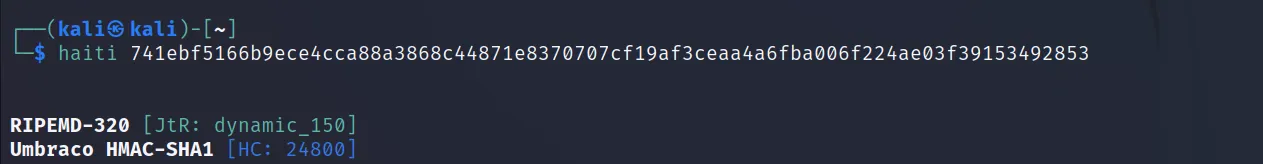
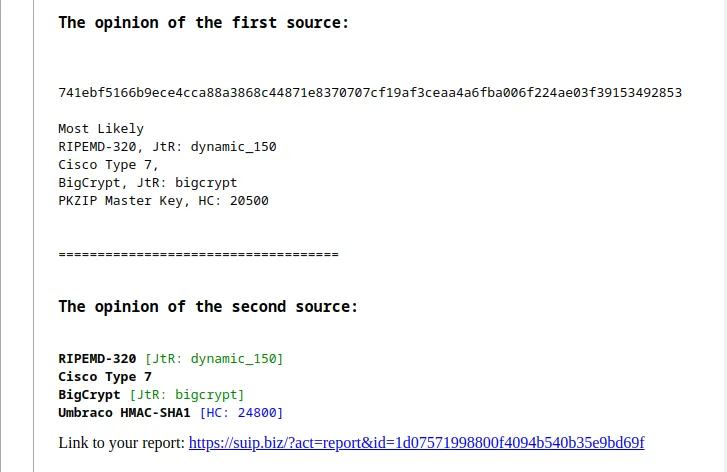
Now use this as ‘haiti <hash>‘ format. For example execute this command
'haiti 741ebf5166b9ece4cca88a3868c44871e8370707cf19af3ceaa4a6fba006f224ae03f39153492853'
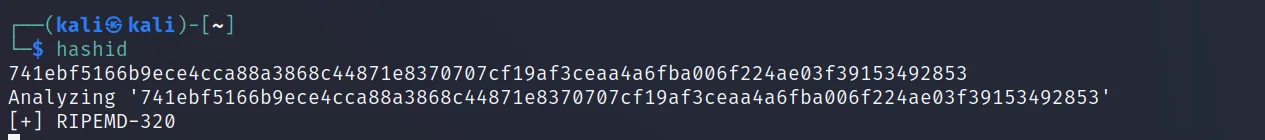
Another tool to include is ‘hashid‘. This tool comes by default installed in Kali Linux. Here we have to give the hash as an input.
These two tools will cover most of the hashes. Now let’s move on to online identifier.
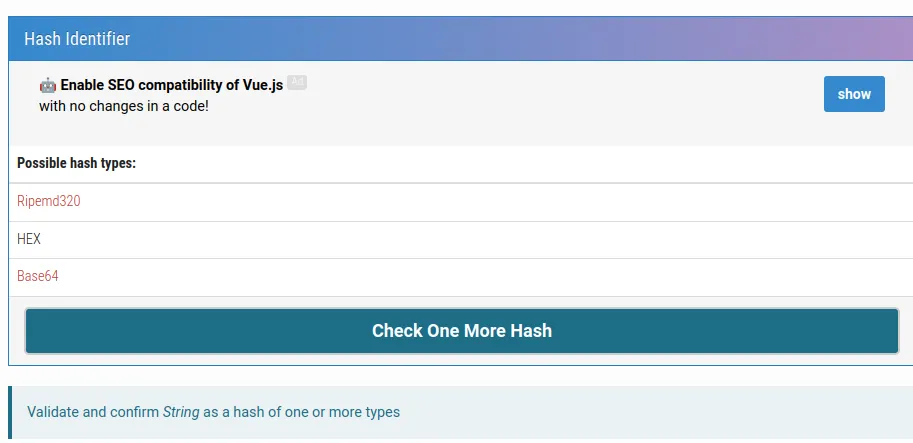
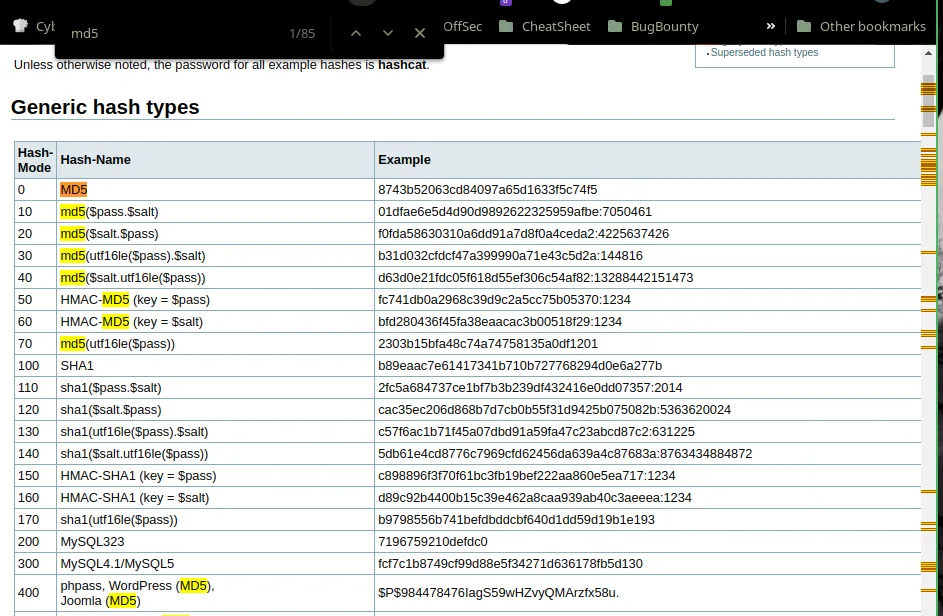
Md5hashingis a very good online tool for identifying the hash types. Look at the result below.
Another tool that we can use for identifying the hash type.
Online tools are very helpful for quick findings.
Now to the next step.
Cracking Hashes
After we have access to a system/application we probably will look for getting access to more resources by finding hash/API/passwords. And one password can be used in multiple services as well. So, if we can crack the hash we will be able to get access to more resources.
Let’s start with john the ripper aka john.
In Kali Linux, it’s by default installed. But if you don’t have it you can download it from Kali Linux repo ‘sudo apt install john‘, and download it from GitHub for other Linux.
The basic structure of john is ‘john –format=<format> –wordlist=<wordlist> <hashfile>‘. The ‘–format‘ is used to set the hash type and the ‘–wordlist‘ is used to include the wordlist.
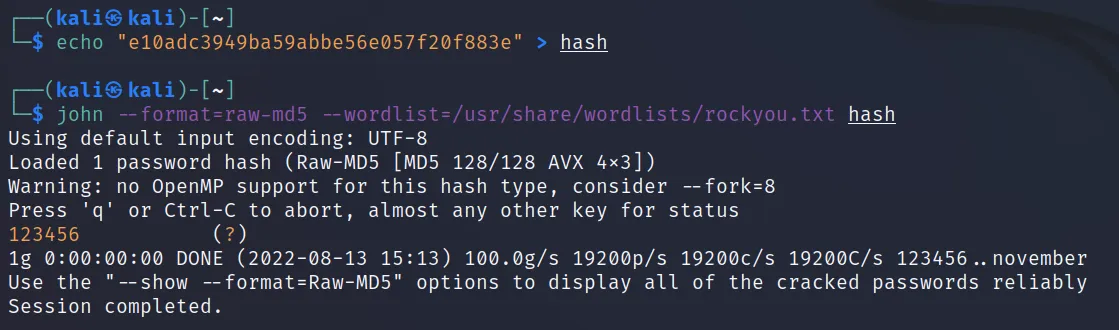
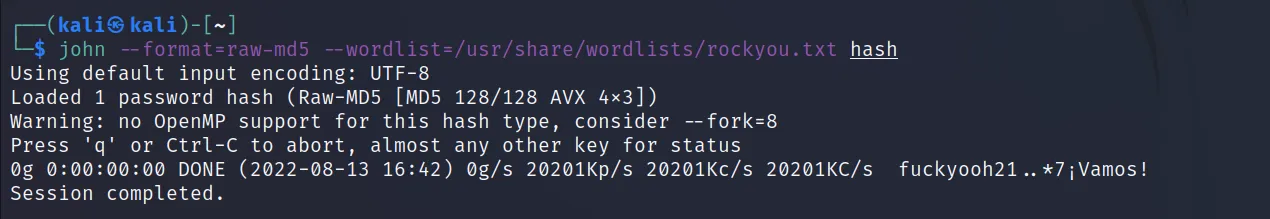
For example, let’s use this hash e10adc3949ba59abbe56e057f20f883e. Save the hash to a file, and execute this command ‘john –format=raw-md5 –wordlist= /usr/share/wordlists/rockyou.txt hash
You will see that the password is cracked. Now how will we figure out the hash format? If you remember, we’ve already gone through identifying hashes. Let’s try that.
Here we are seeing all the outputs because of the possibility. The best thing about this haiti tool is that it also shows us the format for john the ripper aka JtR. But it can be done using the john listing feature as well.
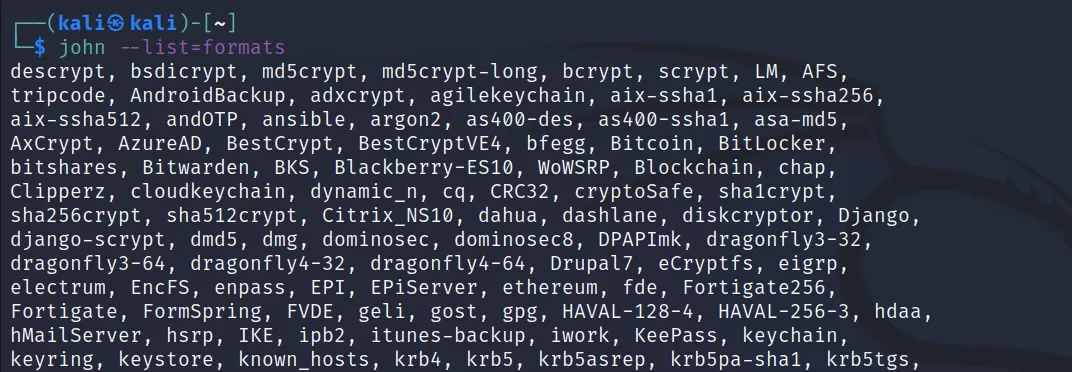
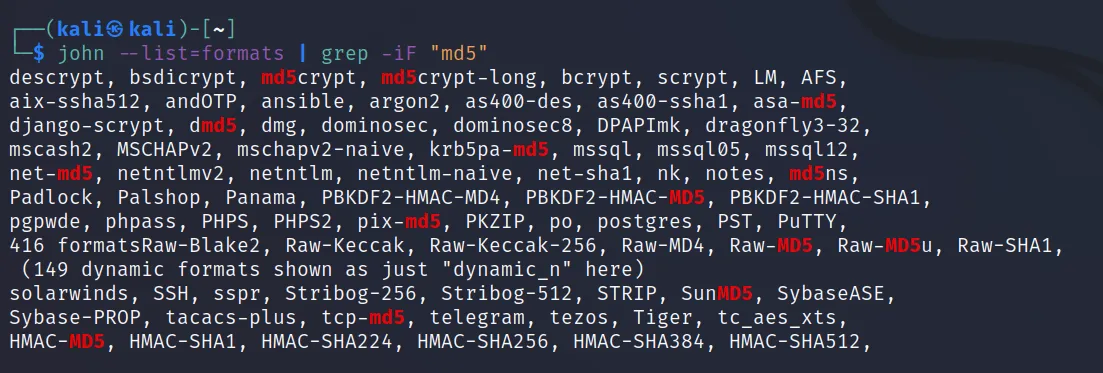
Use ‘john –list=formats‘ for listing the format available in john.
From that we can grep the keyword we have like md5, ‘john –list=formats | grep -iF “md5”‘.
Let’s crack some common hashes.
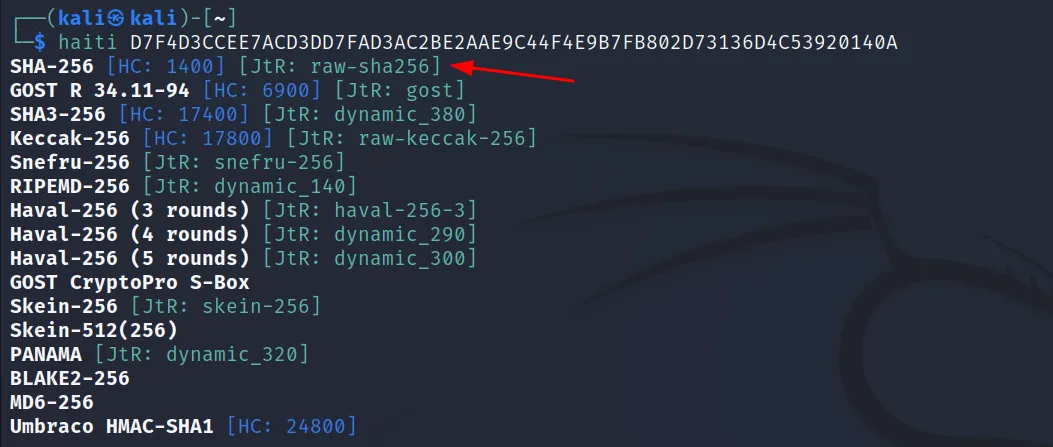
SHA-256
Hash: “D7F4D3CCEE7ACD3DD7FAD3AC2BE2AAE9C44F4E9B7FB802D73136D4C53920140A”
Identifying hash type
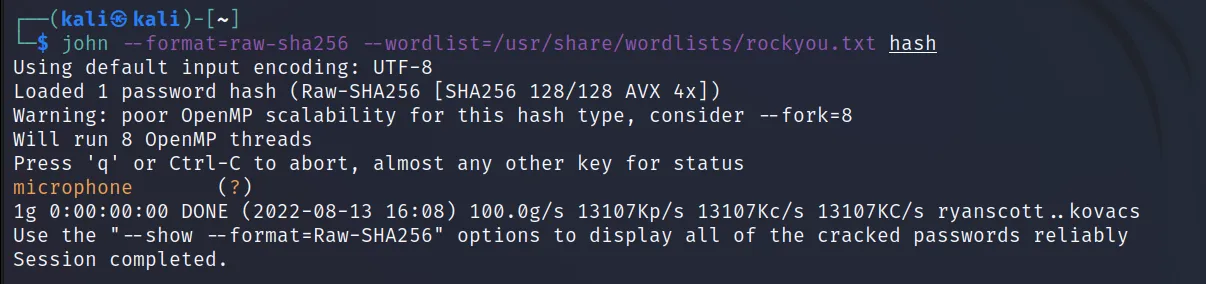
Cracking Hash
Command Executed: ‘john –format=raw-sha256 — wordlist=/usr/share/wordlists/rockyou.txt hash‘
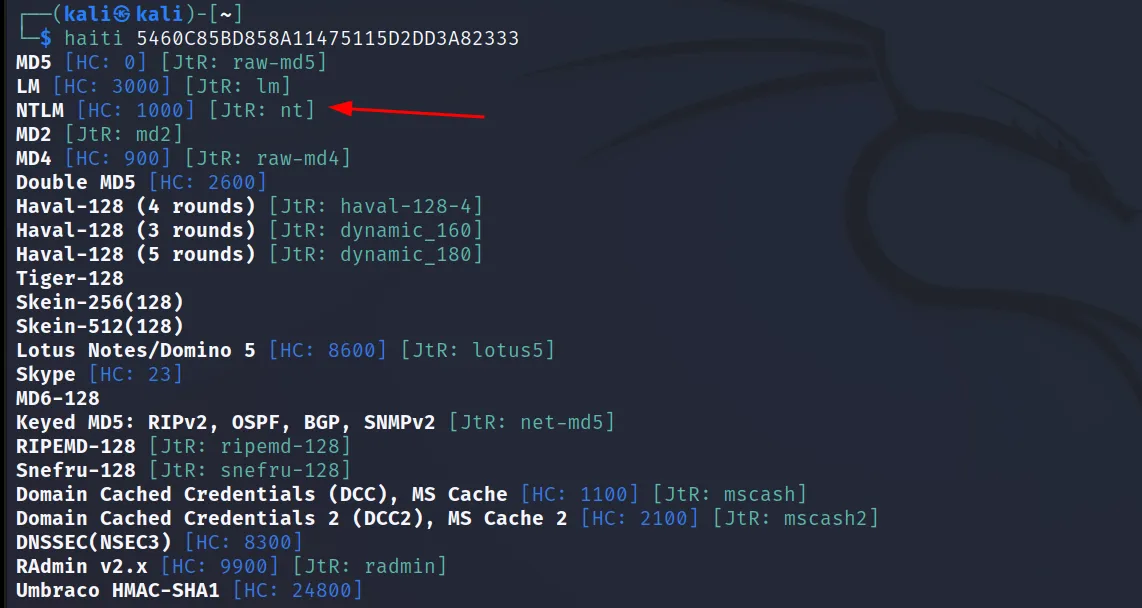
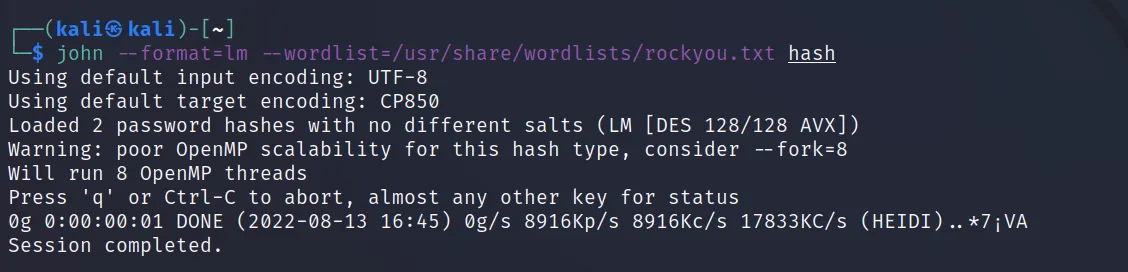
NTLM (Windows password hash type)
After getting access to a windows system using some vulnerabilities. We can dump the Windows User hashes and then crack them to get the password. From there we can establish persistence in the system.
Hash: “5460C85BD858A11475115D2DD3A82333”
But why not MD5? It shows MD5 on the first line. We will find it out when we try to crack it.
What about the next one?
As you can see both failed. So when there are multiple suggestions and the first one doesn’t work we have to check all of them one by one until we find one valid match.
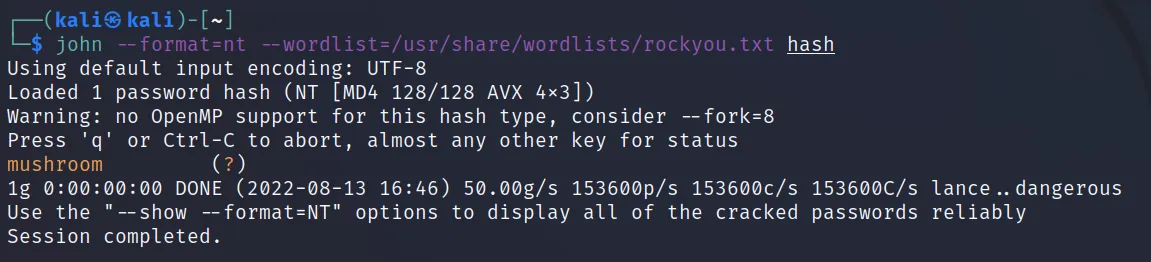
Command Executed: ‘john –format=nt –wordlist=/ usr/share/wordlists/rockyou.txt hash‘
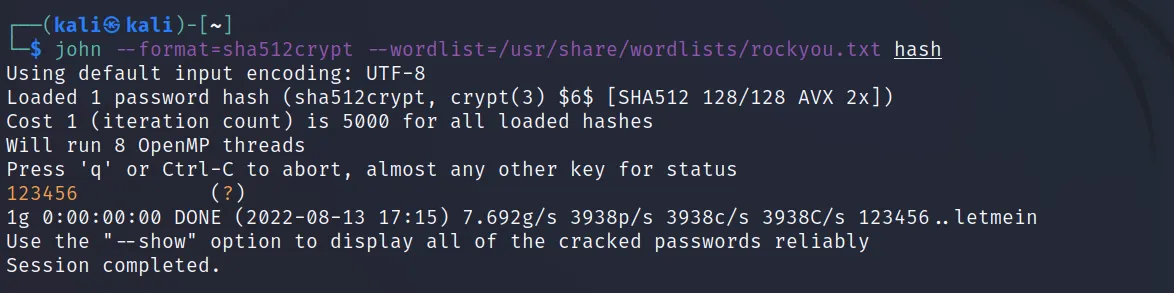
SHA512CRYPT (Linux password hash)
We have already seen the use case of this in our earlier articles. The Linux Distros stores password hashes with SHA512CRYPT. So, cracking it will give us persistence over the system.
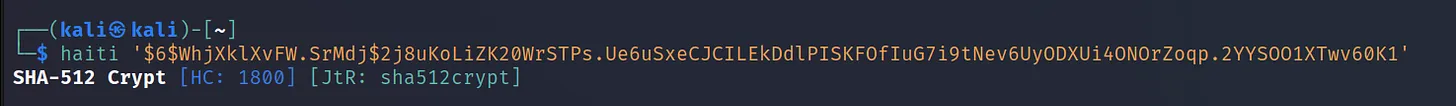
Hash: “$6$WhjXklXvFW.SrMdj$2j8uKoLiZK20WrSTPs.Ue6uSxeCJCILEkDdlPISKFOfIuG7i9tNev6UyODXUi4ONOrZoqp.2YYSOO1XTwv60K1”
Identifying hash type
We have already seen the use case of this in our earlier articles. The Linux Distros stores password hashes with SHA512CRYPT. So, cracking it will give us persistence over the system.
Command Executed: 'haiti '$6$WhjXklXvFW.SrMdj$2j8uKoLiZK20WrSTPs.Ue6uSxeCJCILEkDdlPISKFOfIuG7i9tNev6UyODXUi4ONOrZoqp.2YYSOO1XTwv60K1''
Cracking hash
Command Executed: 'john --format=sha512crypt --wordlist=/usr/share/wordlists/rockyou.txt hash'
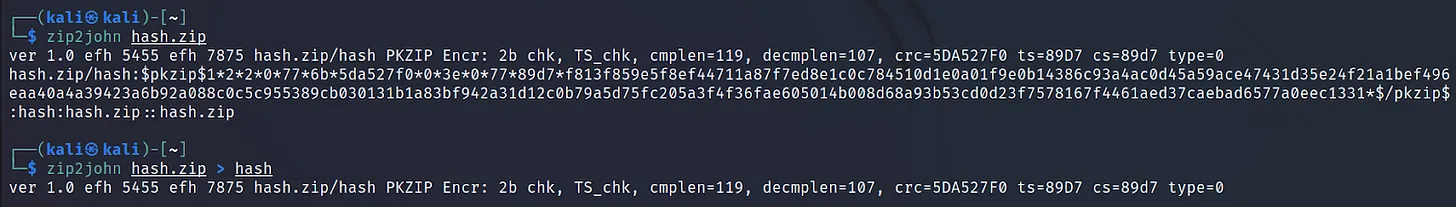
Zip2John
Sometimes we may discover important zip files in a target’s system. And most likely they could be encrypted with a password. We can use this method to crack that password.
Using john we can crack passwords of zip files. John has a method of making hash from an encrypted zip file. Then we can crack this hash with john. This method is so useful. For this, we have to use the john sub tool zip2john.
First, create a zip file with a password. Use this command ‘zip -e hash.zip hash‘ to do that.
Now use ‘zip2john‘ to convert it to the hash.
Command Executed: ‘zip2john hash.zip > hash‘
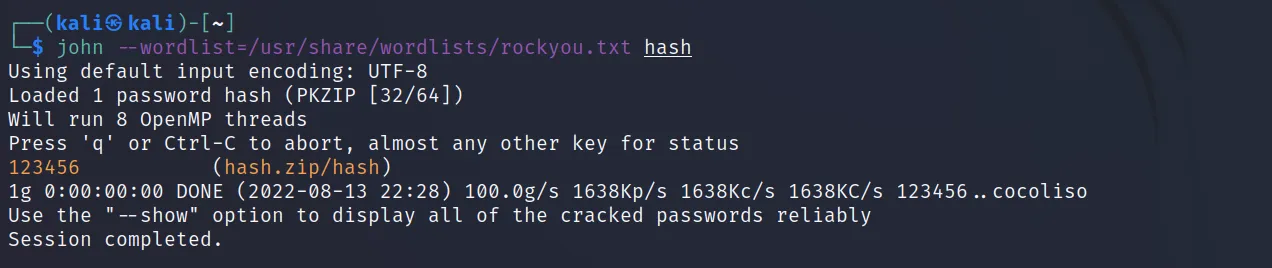
Now let’s crack the hash. Here we need not include the hash type, john will automatically detect it.
Command Executed: ‘john –wordlist= /usr/share/wordlists/rockyou.txt hash‘
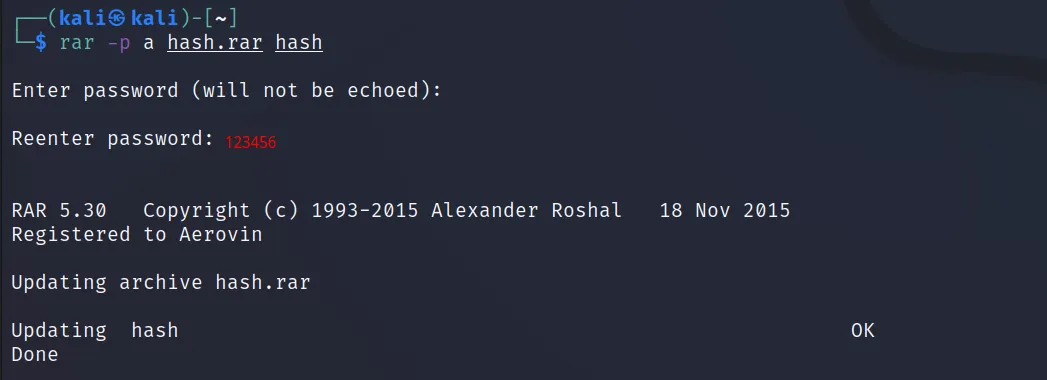
The same can be done using rar files as well. Let’s create a rar file first. We have to install a tool from GitHub to create a rar file. Follow the commands to download and install the tool.
”’
wget https://github.com/ aerovin/winrar/archive/master.zip
unzip master.zip
cd winrar-master
sudo make
sudo make install
cd ..
rm -rf winrar-master
rm master.zip
”’
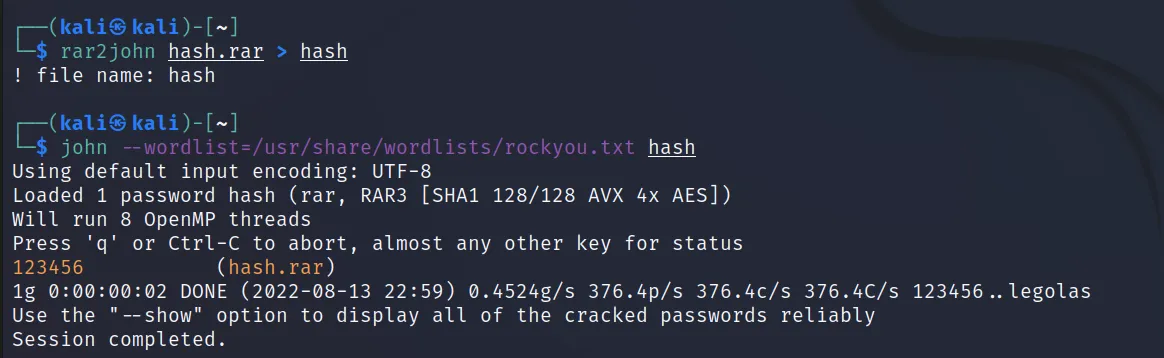
Now execute this ‘rar -p a hash.rar hash‘ command to create a rar file with a password.
Now let’s convert it to john hash, using ‘rar2john hash.rar > hash‘. Let’s crack it using the ‘john –wordlist=/usr/share/wordlists/rockyou.txt hash‘ command.
And the password is cracked.
Cracking SSH Keys
After successfully getting access to a machine. We’ll often discover id_rsa files in the .ssh directory. But in most cases, they are protected with a passcode. Using this method we can get the passcode.
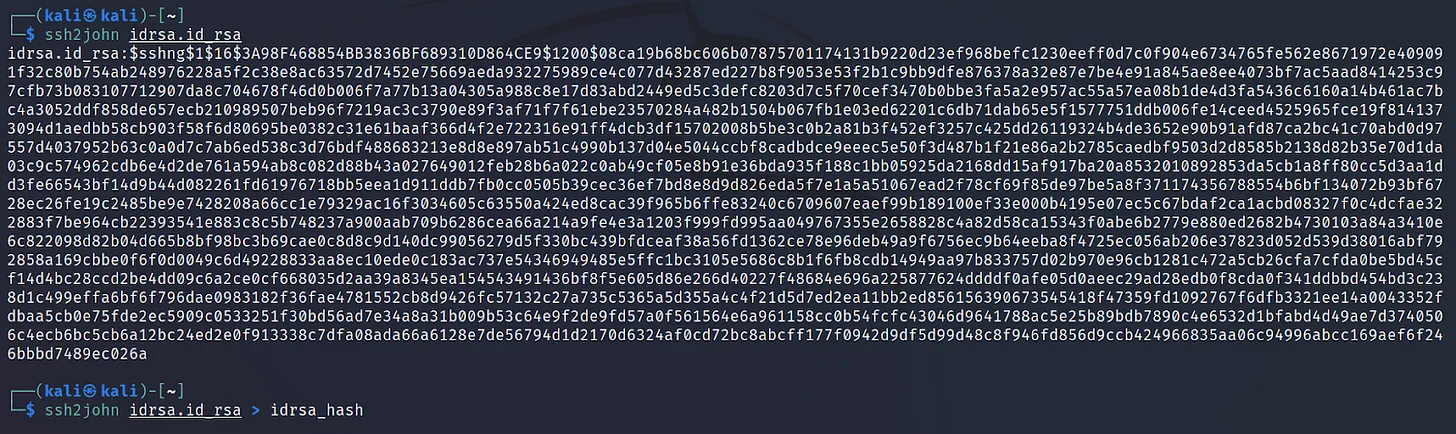
After getting the id_rsa file. Convert it to john hash.
Command Executed: ‘ssh2john idrsa.id_rsa > idrsa_hash‘
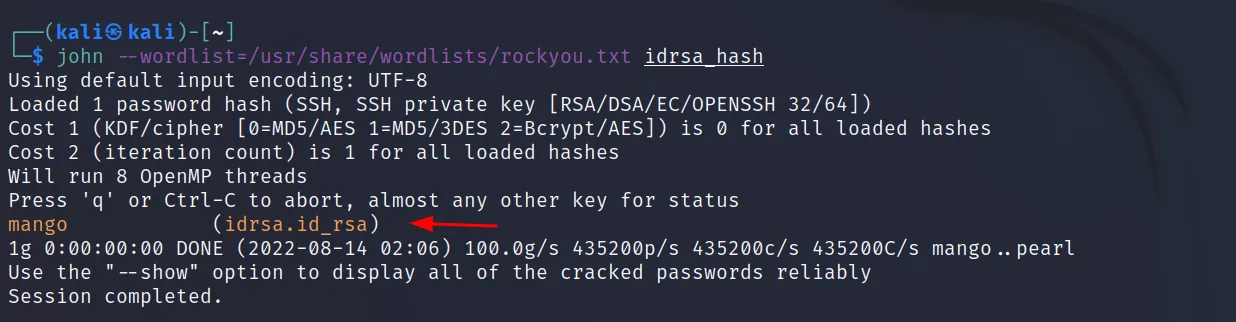
Now let’s crack it using john.
Command Executed: ‘john –wordlist=/usr/share/wordlists/rockyou.txt idrsa_hash‘
Not just them we can also use other john sub tools. Look at the tools below.
Single Crack Mode
It’s a mode where we don’t have to provide any password list. We simply have to provide a wordlist of “username: password_hash” combo and john will use a method called word mangling to generate more words from the given username. For example
If the provided username is hacker, word mangling will be,
- HacKer
- Hack3r
- hacKer$
- hack3r!
And so on.
I hope you got the idea. It creates a password list from the username by adding and modifying it.
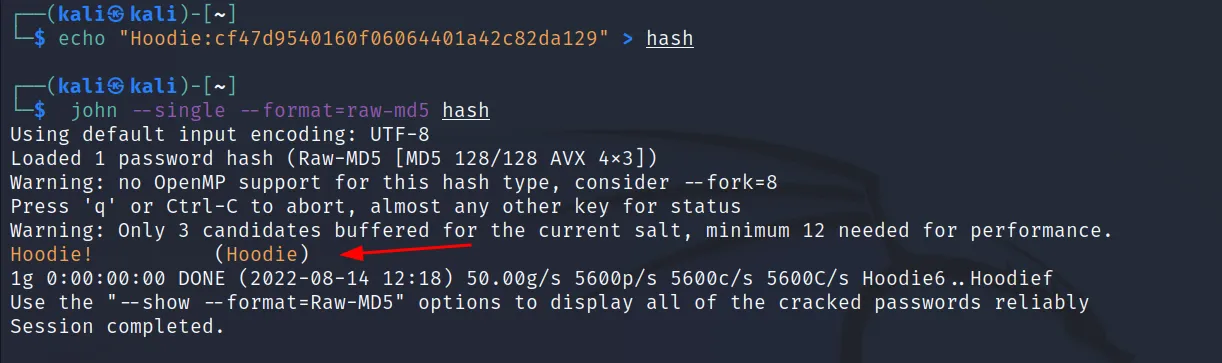
The format will be “Username:HASH” , “Hoodie: cf47d9540160f06064401a42c82da129”.
Syntax: ‘john –single –format=<format> <path to hash_file>‘
The ‘–single‘ will select the mode.
Let’s try to crack.
Command Executed: ‘john –single –format=raw-md5 hash‘
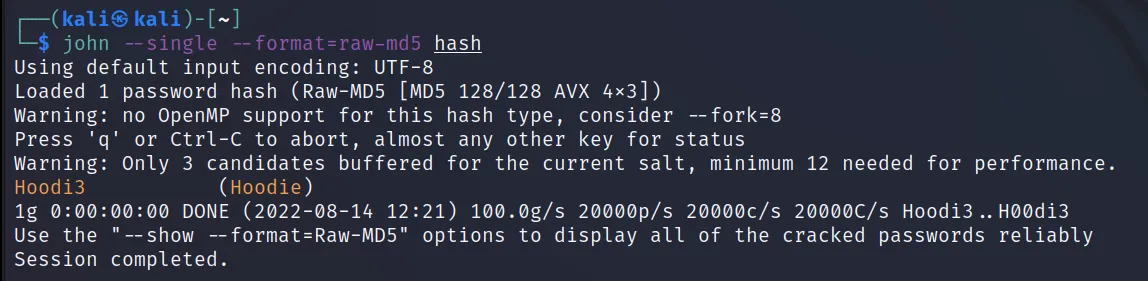
Let’s try a different hash “Hoodie: 689b0eddaf7ca753a4245dd4da360603“.
I hope it’s clear now.
Another interesting feature of john is using rules. What are the rules? Rules are some algorithm that manipulates the password lists. For example, we can add numbers, symbols, or anything on the go when cracking a password.
Most of the time when you try to set a password to a website. If the password contains only letters you will see a warning telling you to use numbers, symbols, capital letters, etc. Now you know that all the passwords from that particular site must have numbers, symbols, etc in them. And in most cases it’s guessable. For example, if the password was “hoodie” the user can pick it as “Hoodie123!@” or something like this.
Using rules you can add the change. Make a capital letter, and add numbers, symbols, or anything at any place in the word list. And john will generate this on the go.
An interesting thing is that you can also create your own rules, and also can use pre-built rules.
The file ‘/etc/john/john.conf‘ contains all the rules.
Let’s create a custom rule and use it.
Our password will be “Hoodie9!”, We will take the first 100 words from rockyou.txt and add the hoodie word to the end.
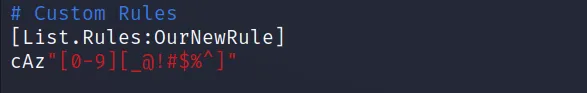
Now add the following to john.conf
”’
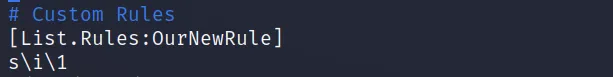
[List.Rules:OurNewRule]
cAz”[0-9] [_@!#$%^]”
”’
Breakthrough
[List.Rules:OurNewRule], This is the pattern of using a custom rule, “OurNewRule” is the place where you will put the rule name.
c is a command that capitalizes the first letter.
A is for appending, and z means the end of the word. Az means specified characters will be appended at the end of the word. The specified words here are 0-9 and some symbols. This must be in “”, [].
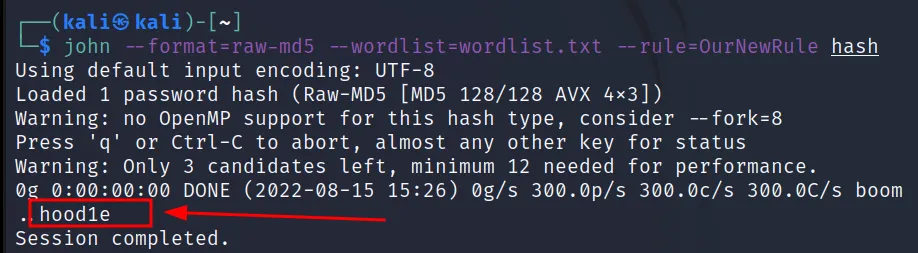
Now let’s crack,
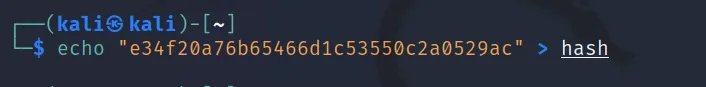
Hash: “e34f20a76b65466d1c53550c2a0529ac”
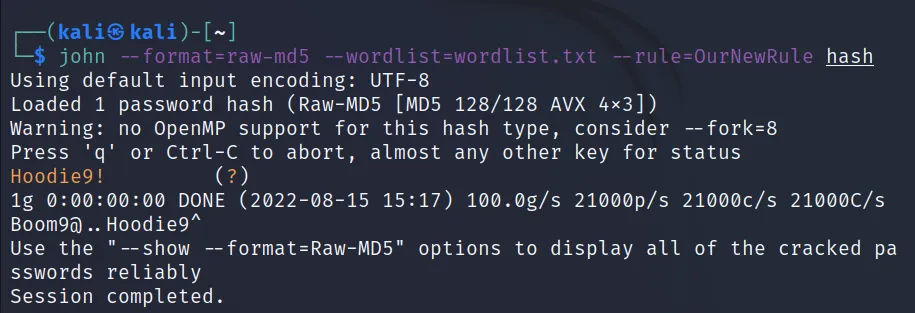
Command Executed: ‘john –format=raw-md5 –wordlist=wordlist.txt –rule=OurNewRule hash‘
Bingo 🙂
Let’s learn a little more.
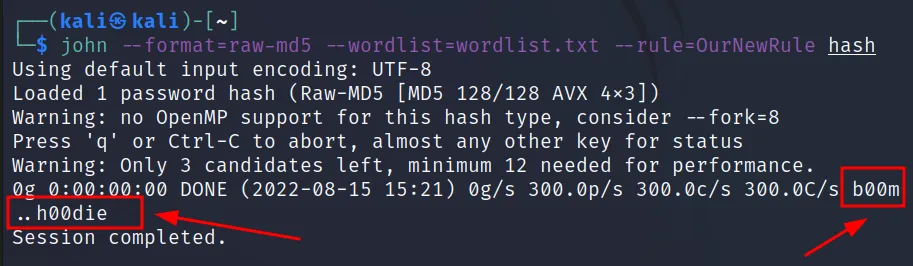
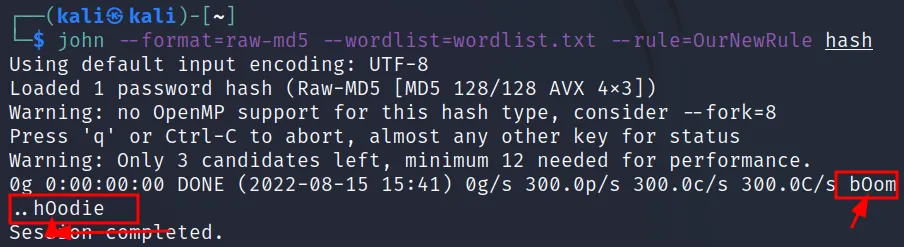
What if we want to replace the o with 0?
we can follow the command “s” this will replace characters A to B. We have to use it as, s\A\B.
Let’s see it in action.
I used the wrong hash. Because when experimenting we probably won’t like to generate hashes every time. Once a hash is cracked it cannot be cracked again by john unless we remove the stored data. So trying with a wrong hash or a hash in which plain text will not be in the wordlist will help us save time.
Instead, John provides the last two words from that generated list, we can look at that.
As you can see the o is converted with 0. Let’s try to convert i with 1.
And you will see it’s successfully converted i to 1.
Now instead of capitalizing the first character, what if we want to change the 2nd letter to upper case?
T<Position_of_character>, T1, it changes letter cases of the given position. It will turn lower case to upper case and vice versa. The position for indexing should start from 0.
You can check about john’s rule on the official rule page here for more information.
John conf also has some predefined rules that you can look at and try to understand from the output.
Now experiment with them. Believe me, creating a custom rule for the first time will not be easy, don’t give up. You can do almost any change. But mostly you don’t need to do it, only adding, or changing some characters will do the job.
One interesting fact, my VM username is mr_gr33n and my password is Mr_Gr33n. See how I am vulnerable to this attack.
Enough about john, Let’s move on to the fastest hash cracker available. Yes, it’s hashcat. And the reason it’s first is that it can use Cuda core from your GPU. The CPU usually has very few cores and threads. Compare that to a Decent Entry Level GPU has 100x+ more core than a CPU.
This is why GPUs are used for crypto mining.
We have already used hashcat several times in our CTFs.
The basic syntax for hashcat is:
‘hashcat -m <mode_num> <hash_file> <wordlist>‘
You will find all the modes available on the wiki example page of hashcat, or the help menu. From there you can check or search the hash you’ve identified.
And you will also see the mode number. Let’s crack an md5 hash.
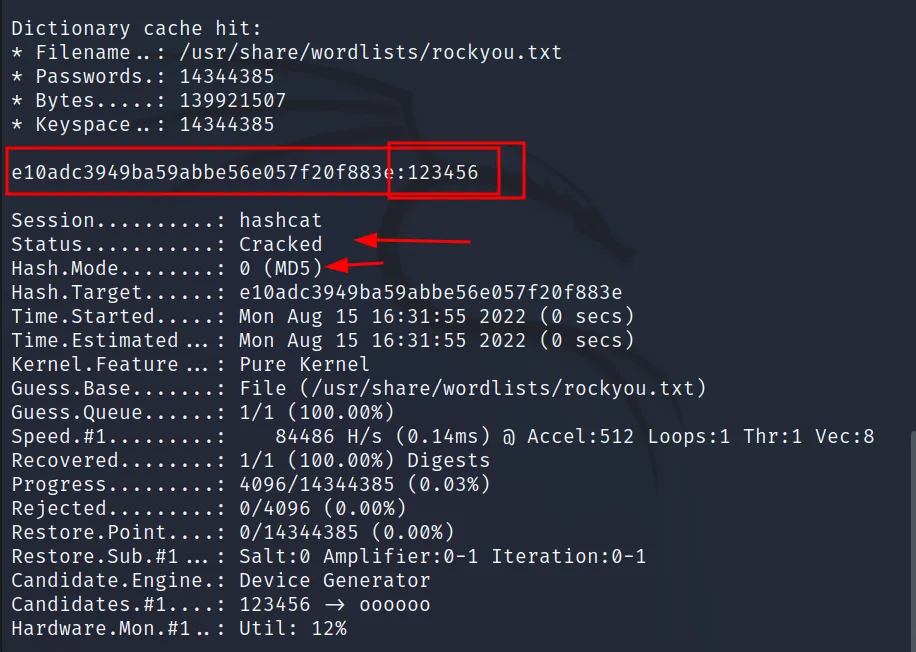
Command Executed: ‘hashcat -m 0 hash /usr/share/wordlists/rockyou.txt‘
And the hash is cracked. The reason why it took less than a second is that the password is on the first line of rockyou.txt.
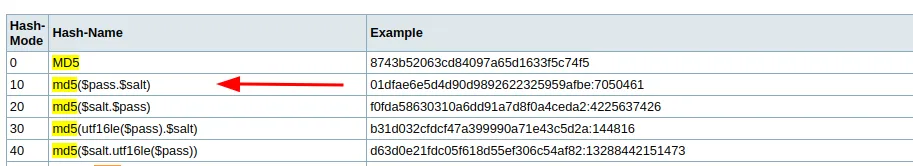
Let’s try cracking hashes with salt. First identify the hash type, and mode.
It’s showing the type also with the hashcat mode. But since it’s salted we have to look for md5 with the salt mode on the example page.
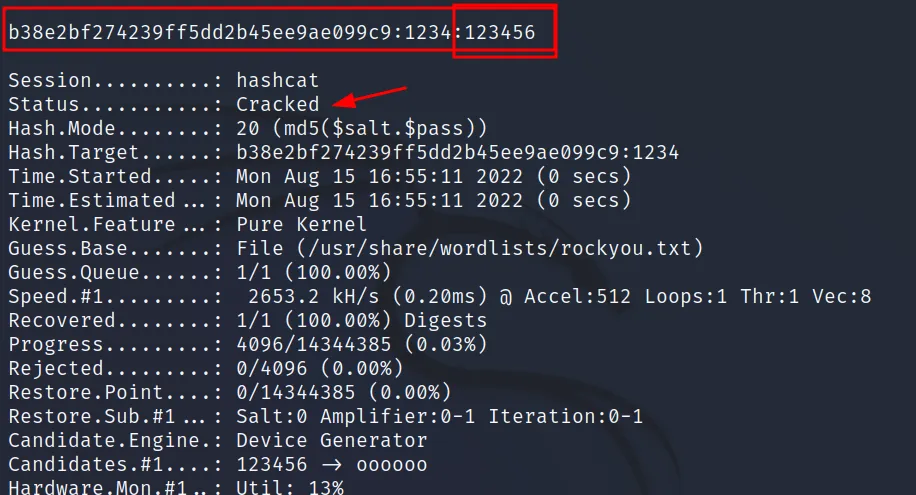
Hash: “b38e2bf274239ff5dd2b45ee9ae099c9”
Salt: 1234
The hash mode number is 10. And the pattern is first the hash then a colon then the salt.
So Hash with salt: “b38e2bf274239ff5dd2b45ee9ae099c9: 1234”
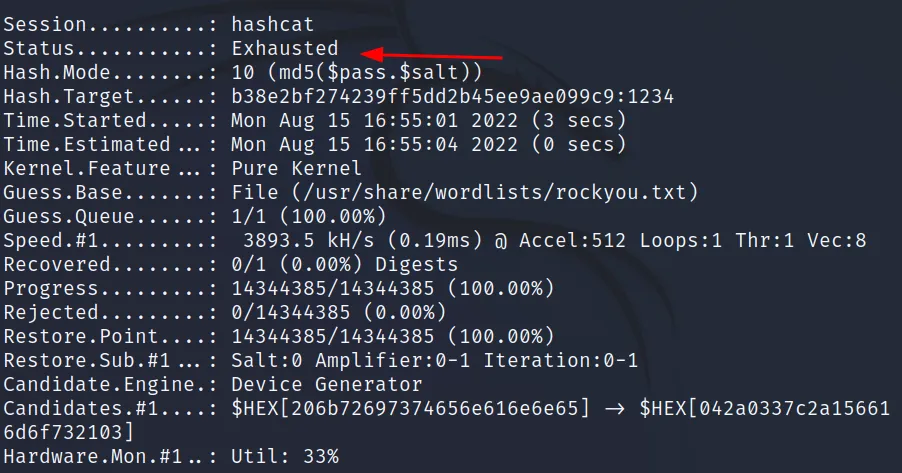
Command Executed: ‘hashcat -m 10 hash /usr/ share/wordlists/rockyou.txt‘
Seems this mode didn’t work, But we still have another one 20, let’s try that.
Command Executed: ‘hashcat -m 20 hash /usr/share/wordlists/rockyou.txt‘
This time it worked and the password has been revealed.
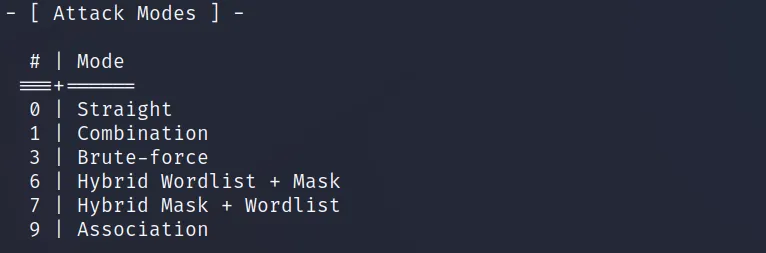
Hashcat has many attack modes. You will find out why attack mode is used in the examples.
The available modes are,
And the attack mode is defined using the ‘-a‘ switch.
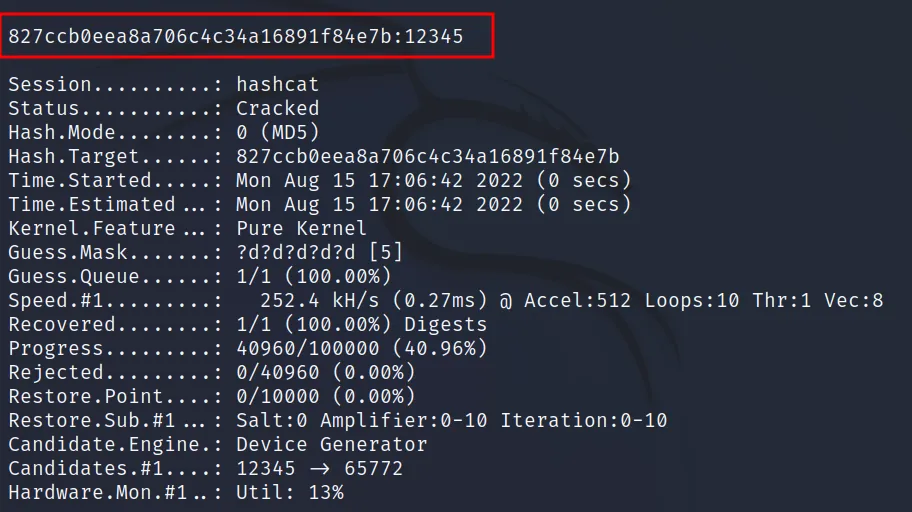
Let’s crack a hash using brute force mode (3).
Hash: “827ccb0eea8a706c4c34a16891f84e7b”
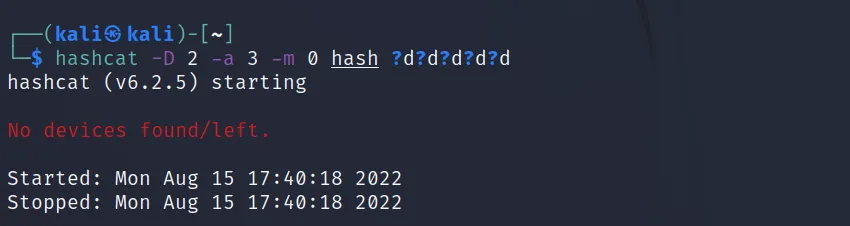
Command Executed: ‘hashcat -a 3 -m 0 hash ?d?d?d?d?d‘
Command Breakthrough
-a is used to define the attack mode
-m is used to define the hash mode
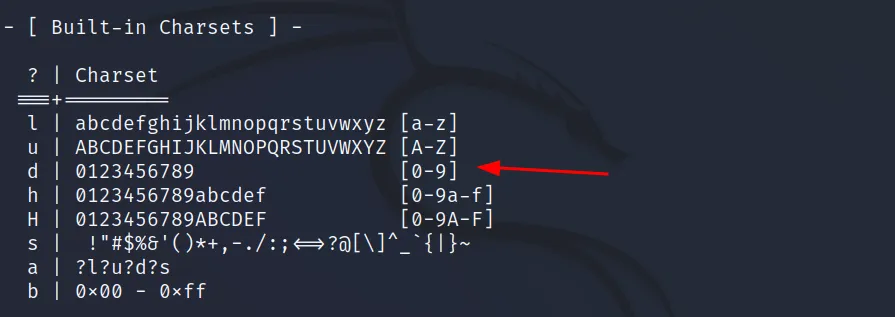
Now ‘?d?d?d?d?d‘ represents 5 character long decimal values. Hashcat has some built-in charset in it.
We can select any of the charsets, we just have to use “?” in front of it. And we have to repeat “?d” or whatever, the number of brute force length. For example,
1234, length 4, so, ?d?d?d?d
password, length 8, so, ?l?l?l?l?l?l?l?l
I hope you got the idea.
Hashcat also has rules like john, and you can also make them. Using and creating hashcat rules are much easier than john (my opinion, may differ for people). Here I am not going to show how to create rules for hashcat.
If you want to create rules on your own, check this official doc and try it out yourself.
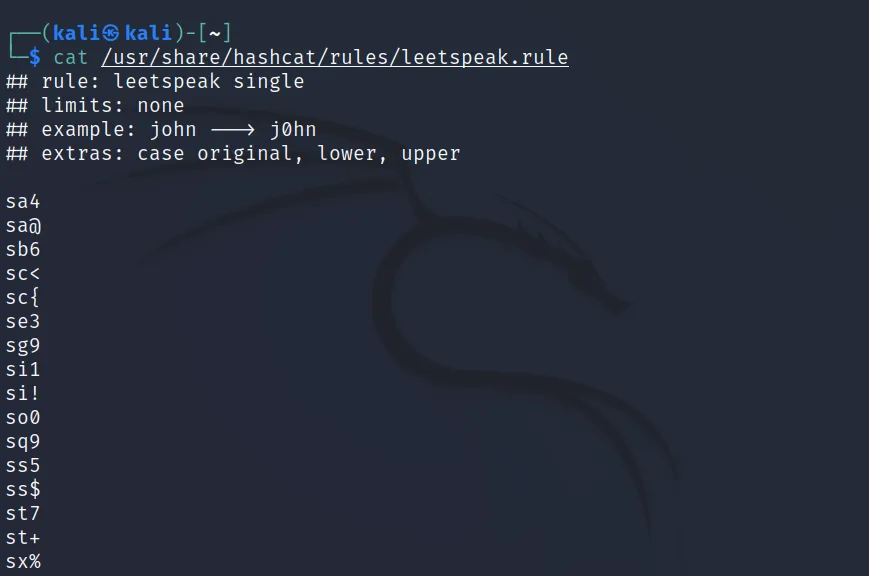
Let’s use one of the pre-built rules and try to understand it. The rule we are going to use here is “leetspeak”, which changes letters to similar-looking numbers.
The first “s” is used to replace the character, just like john’s rule. And the format is ‘s<original_character><character_to_be_replaced_with>‘, sa4 will replace a with 4.
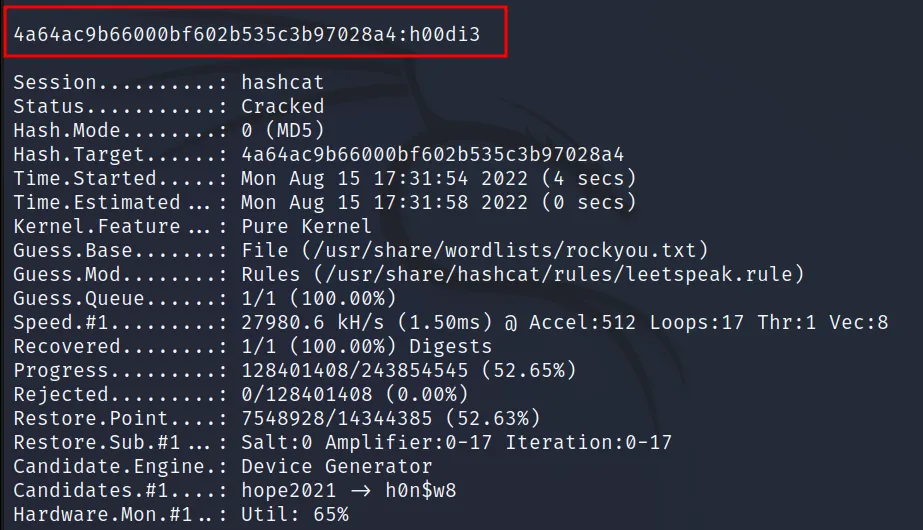
Hash: “4a64ac9b66000bf602b535c3b97028a4”
Command Executed: ‘hashcat -a 0 -m 0 hash /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/leetspeak.rule‘
Now all the time hashcat was using CPU, how are we going to use a GPU?
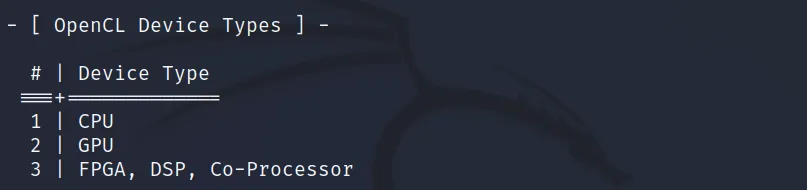
We have to specify the device using the ‘-D <type>‘ switch. The available device types are.
As I don’t have a GPU yet, it’s showing No device found.
But if you have one it will work. GPU is not so much needed in hacking unless hash cracking. As it’s a very small part of hacking, you need not worry much if you dont have one.
There is so much to learn about hashcat/john. I believe at this point you are capable enough to learn them on your own. Always check the help menu/online docs for any assistance.
Online Tool
Sometimes online tools offer the best and fast output compared to offline tools. The offline tools first generate a word into a hash and then matches the hash, which takes much time. Where online tools directly match the hash and deliver the output. The drawback is that you will have limited and most common pre-cracked hashes in online tools.
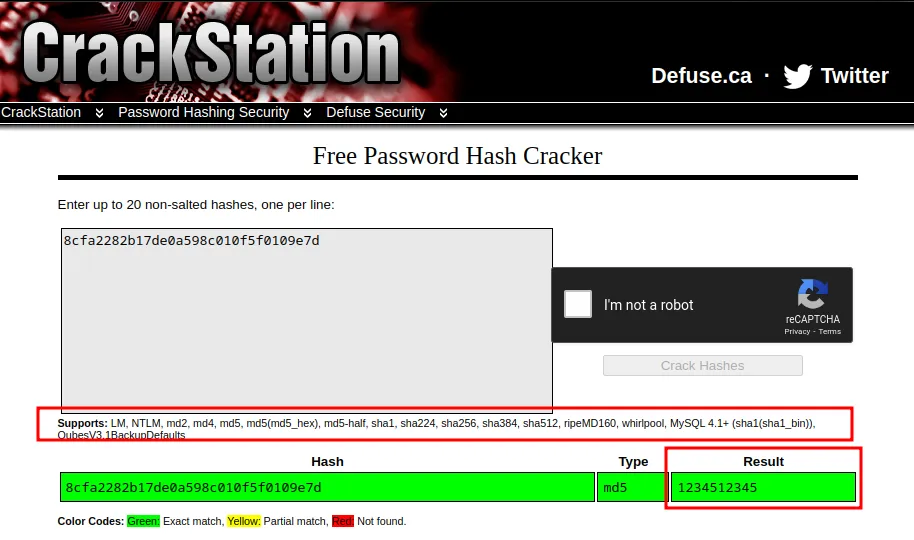
CrackStation
One of the most famous, and used online cracking tool for hackers. You can see the supported hashes on the site.
Well, there is not much to explain about it. Just go there and paste the hash. If you are lucky a match will be found.
Final Words
Well, Hoodies! It was a long one. Don’t rush, give it time. You will do it for sure. I hope you found this article useful. For any question, I am always there for you.
Let us know your opinion about our red team series. And share this with others. It is your support that motivates us to create this kind of article. See ya soon. Best wishes.
HoodieX
Cyber is so much fun. If you loved what you read, then you’re on the right career track.
That’s all for this one.
Keep grinding, Hoodies.
WAGMI
Your fren,
-Cyber