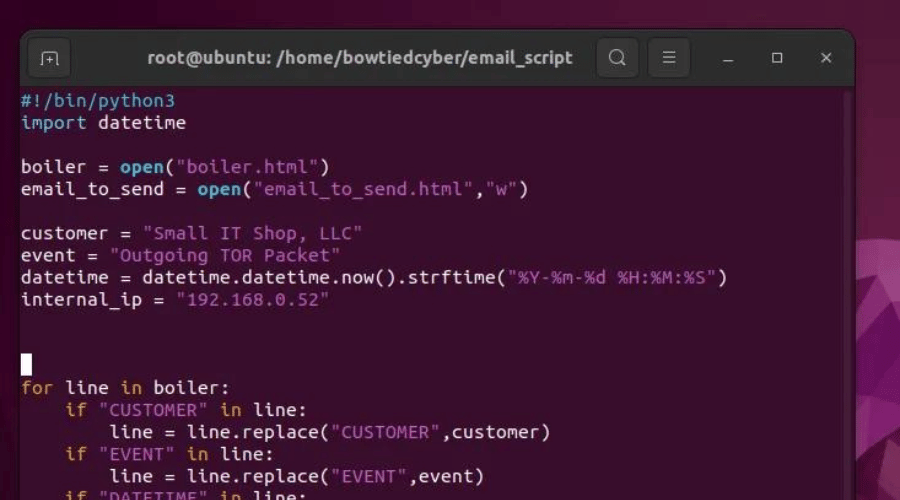
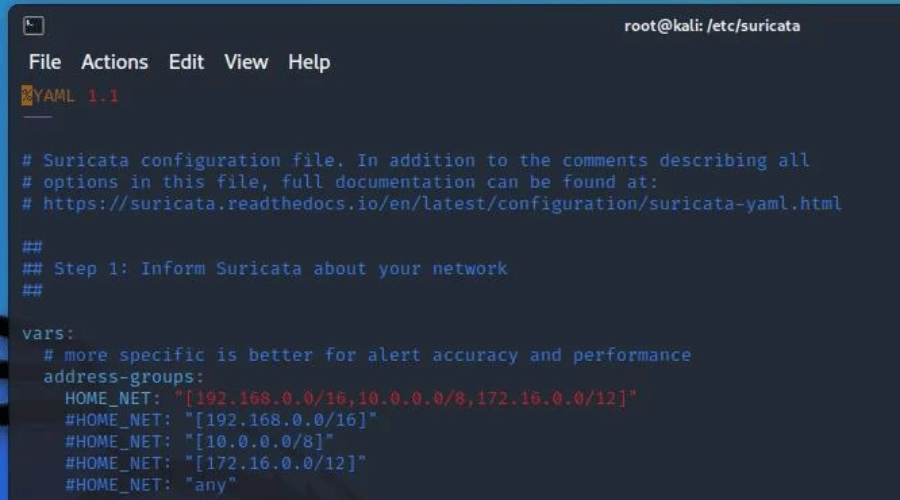
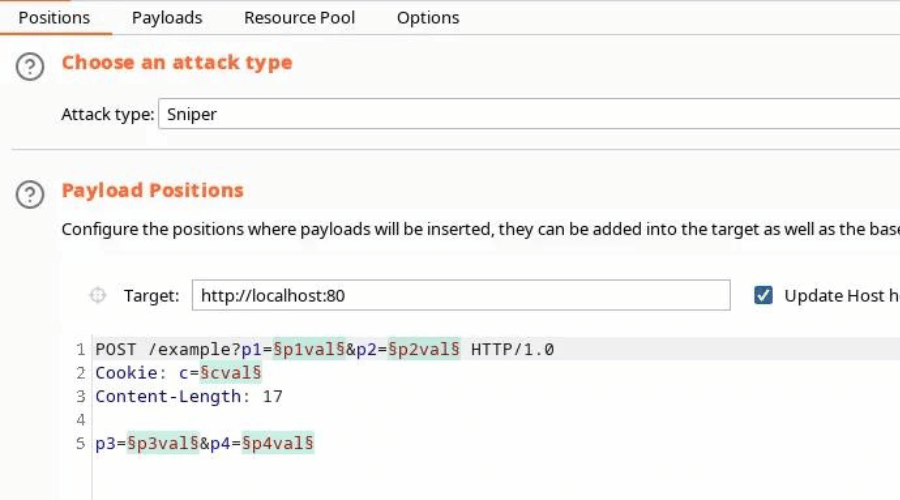
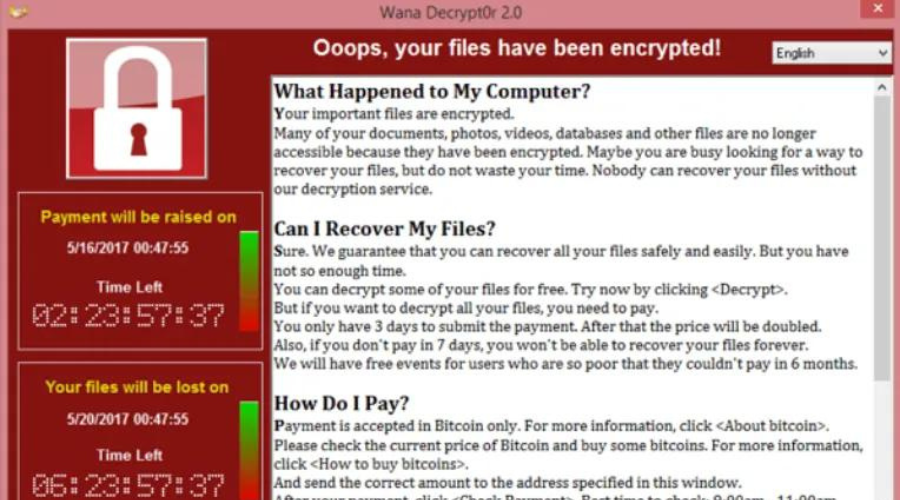
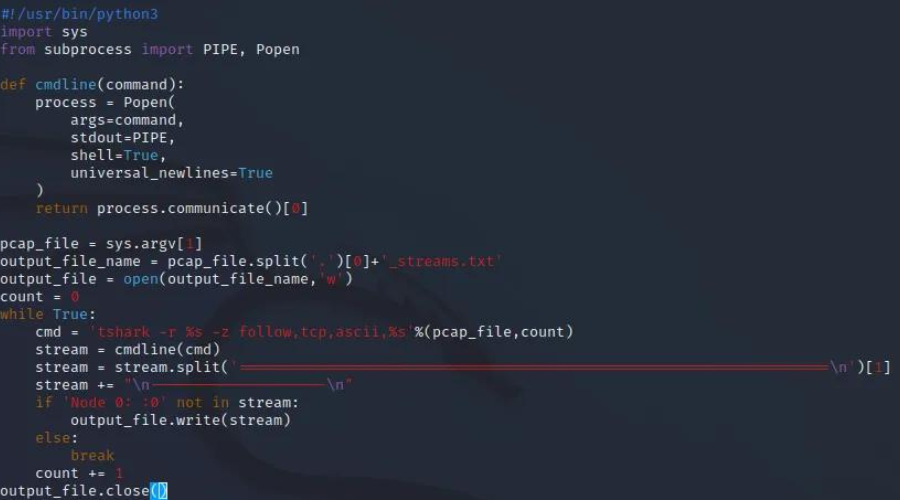
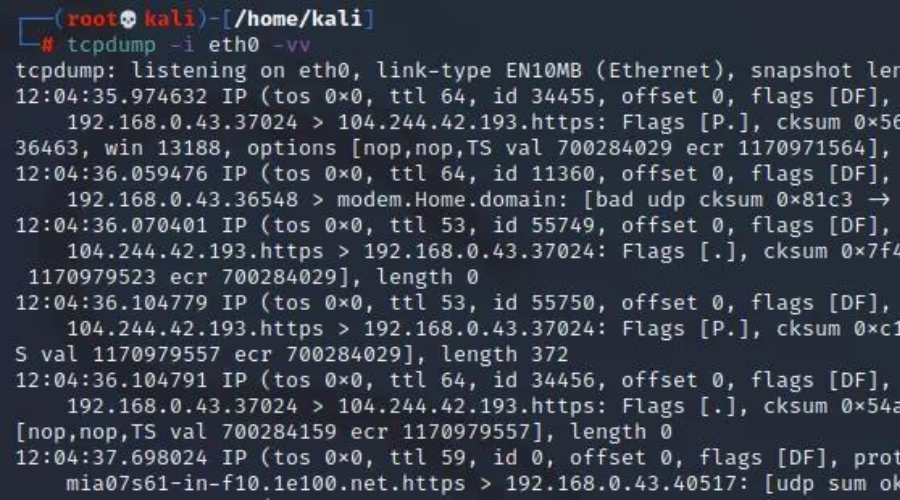
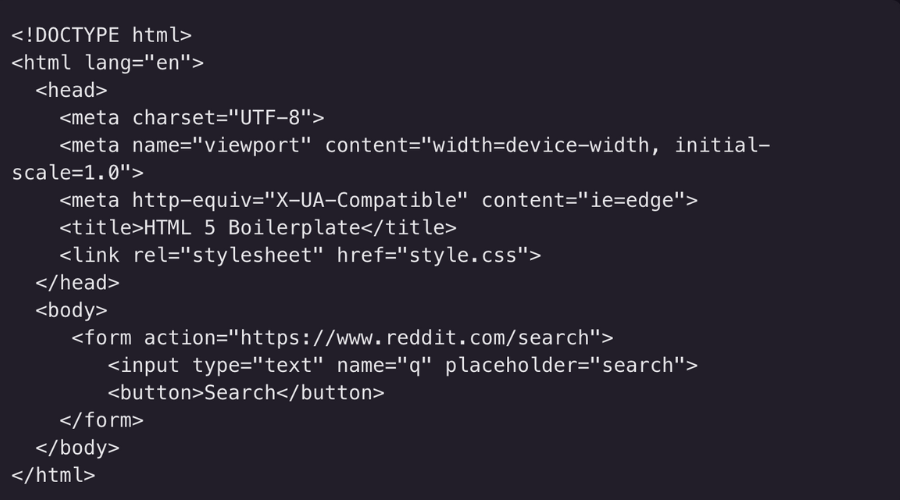
Get the full archive of everything you need to go from ZERO to HOODIE and land a job in cybersecurity in as little as 90 days.
So far, we’ve helped out students win over $1.6M in total comp. This method works.
What you get with a FREE subscription:
What you get with a PAID subscription: